As organisations expand, the necessity of securely migrating data across AWS accounts becomes a paramount concern. Amazon S3 Cross-Region Replication (CRR) emerges as a robust solution, allowing organisations to seamlessly and securely transfer data between S3 buckets in different AWS regions. This comprehensive blog will elucidate each step involved in migrating S3 data across accounts using S3 Cross-Region Replication, delving into policy details and security considerations for a meticulous and secure data migration.
Prerequisites:
Before embarking on the migration journey, ensure the following prerequisites are meticulously fulfilled:
1. AWS Accounts: Set up source and destination AWS accounts, each with tailored permissions for S3 and IAM.
2. S3 Buckets: Establish source and destination S3 buckets in their respective AWS accounts.
3. IAM Roles: Craft IAM roles, meticulously defining permissions to facilitate secure communication between the source and destination accounts.
Step-by-Step Guide:
Step 1: Configure IAM Roles:
Source AWS Account:
– Create an IAM role named, for example, “S3ReplicationSourceRole.”
– Attach a policy allowing read access to the source S3 bucket
 .
.
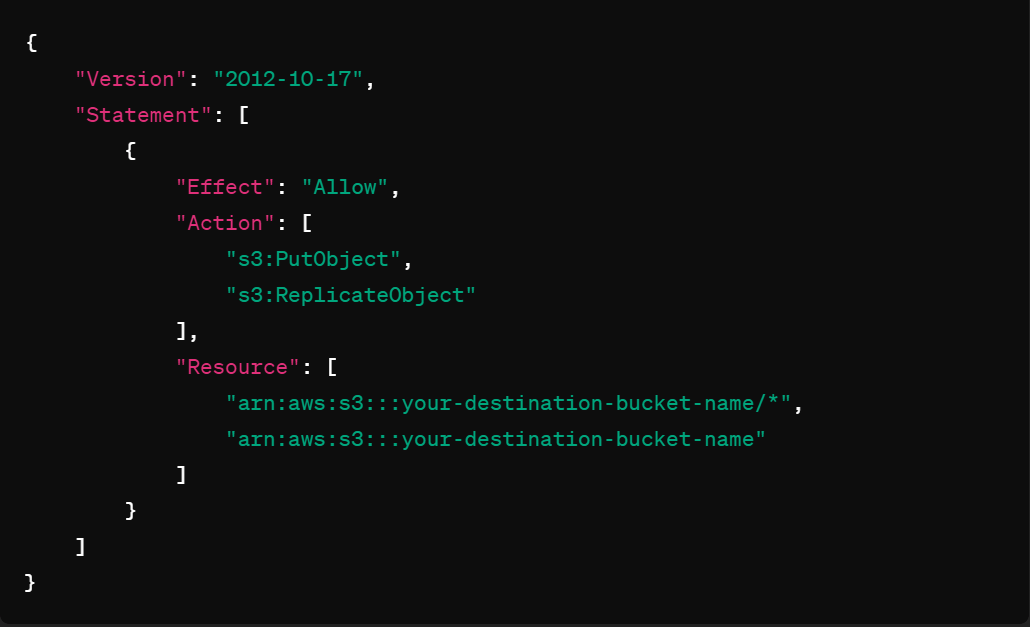
Destination AWS Account:
– Create an IAM role named, for example, “S3ReplicationDestinationRole.”
– Attach a policy enabling write access to the destination S3 bucket.
Step 2: Enable Versioning:
Source and Destination S3 Buckets:
– Enable versioning to ensure all versions of objects are replicated.
– This is crucial for maintaining data integrity during and after the migration.
Step 3: Configure S3 Cross-Region Replication:
Source AWS Account:
– Navigate to the S3 bucket settings and select the “Management” tab.
– Under “Replication,” click “Add Rule” to create a new replication rule.
– Define the source and destination buckets and specify the IAM role created in the destination account.
– Optionally, set up replication filters based on your requirements.
– Save the replication rule.
Step 4: Verify and Monitor Replication:
Monitor Replication Status:
– Regularly check the replication status in the S3 bucket’s “Management” tab.
– Observe the “Metrics” tab for CloudWatch metrics related to S3 replication.
Set Up CloudWatch Alarms:
– Configure CloudWatch Alarms to receive notifications for any replication errors or issues.
– This ensures prompt detection and resolution of potential problems.
Step 5: Validate Data Integrity:
Regular Validation:
– Periodically validate data integrity by comparing objects in the source and destination buckets.
– Use checksums or AWS S3 Inventory for comprehensive validation.
Step 6: Cleanup and Post-Migration:
Application and Workflow Updates:
– Update applications or workflows to utilise the destination bucket once data replication is verified.
Considerations for Source Bucket:
– Depending on your migration strategy, consider deleting the source bucket or specific objects to complete the migration.
Advanced Considerations:
Logging and Auditing:
1. S3 Access Logging:
– Implement S3 access logging to monitor and audit S3 data access and replication activities.
2. CloudTrail Logging:
– Enable CloudTrail logging to track API activity related to S3 replication, enhancing security and accountability.
Error Handling:
1. CloudWatch Alarms:
– Fine-tune CloudWatch Alarms to send notifications for replication errors, ensuring swift investigation and resolution.
Cross-Account Resource Sharing:
1. IAM Policy Refinement:
– Review and refine IAM policies to adhere to the principle of least privilege, restricting access to only necessary resources.
Conclusion:
Effectively migrating S3 data across AWS accounts using S3 Cross-Region Replication demands a meticulous and detailed approach. By following each step outlined in this guide and paying close attention to policy details and advanced considerations, organisations can ensure a secure, efficient, and error-free data migration process while upholding the integrity and security of their valuable data throughout the entire transition.
