A cloud risk assessment is, at its core, a structured way to find, analyse, and rank the threats and weak spots lurking in your cloud environment. Think of it as a fundamental security health check that shifts your organisation’s mindset from simply reacting to problems to proactively preventing them. It’s all about protecting your data, staying on the right side of regulations, and making sure your business can weather any storm.
Why a Cloud Risk Assessment is Non-Negotiable for Indian Businesses
Moving to the cloud can supercharge growth, but it also throws open the door to a whole new world of security challenges. Your old, on-premise security playbook just won’t cut it anymore. For businesses across India that are rapidly going digital, this isn’t some far-off, theoretical issue—it’s a real and present danger. Running a regular, in-depth cloud risk assessment has moved from being a “nice-to-have” best practice to an essential investment in your company’s survival.
The moment you adopt the cloud, your security perimeter is redrawn. You’re no longer defending a single castle with a moat and drawbridge. Instead, your critical assets are spread across a vast, shared, and constantly changing landscape. This new reality is complex and demands a specialised way of thinking about risk.
Keeping Pace with India’s Threat Landscape
Cybersecurity attacks are no longer a one-size-fits-all affair; they are increasingly sophisticated and specifically targeted. In India, the threat landscape is now overwhelmingly dominated by cloud-related risks, which are expected to account for a staggering 62% of all detections by 2025. This isn’t surprising when you consider the breakneck speed of digital transformation here. Attackers are taking full advantage of this shift, with Trojans (43.25%) and infectors (34.10%) being common culprits, often masquerading as harmless software to sneak into cloud systems. It’s worth exploring more on these cybersecurity trends in India to truly grasp the changing nature of these risks.
Ransomware, in particular, remains a vicious threat. While one ransomware incident pops up for every 595 total detections in India, the game has changed. Attackers are now more likely to steal sensitive data and threaten to leak it—a tactic called data extortion—rather than just encrypting your files. This shift makes a proactive cloud risk assessment absolutely critical for building a solid defence.
A cloud risk assessment forces you to look beyond just the technical flaws and consider the real-world business impact. It helps you answer the most important question: “What is the actual, tangible risk to our operations, reputation, and bottom line if this particular cloud service gets compromised?”
More Than Just a Compliance Headache
Sure, meeting regulations like the Digital Personal Data Protection Act (DPDPA) is a huge motivator. But the real value of a cloud risk assessment goes much deeper than just ticking a compliance box. When you have a solid assessment process, you build incredible trust with your customers and partners. It shows them you’re serious about protecting their data.
It also makes your operations run smoother. By rooting out misconfigurations, spotting over-provisioned (and expensive) resources, and tightening up sloppy access controls, you can achieve some serious wins:
- Cut down on costs: Stop wasting money on cloud resources you don’t need and avoid the financial penalties that come with insecure setups.
- Boost business continuity: Find the single points of failure in your cloud architecture before they cause an outage and build disaster recovery plans that actually work.
- Build a security-first culture: The process naturally brings together teams from IT, DevOps, legal, and business, giving everyone a shared sense of ownership over security.
When Indian businesses start seeing cloud risk assessment as a strategic advantage instead of a chore, everything changes. You’re not just protecting your organisation; you’re building a more secure, efficient, and trustworthy foundation that allows you to innovate with confidence.
Laying the Groundwork for a Successful Cloud Assessment

Any effective cloud risk assessment stands on a solid foundation of careful planning. This isn’t just about ticking boxes. This is where you connect your security work to what the business actually cares about, ensuring the results are genuinely useful and lead to real action. If you skimp on this groundwork, you’ll end up with an assessment that’s either too broad, too narrow, or completely disconnected from the things that truly matter to your organisation.
The journey starts by defining a clear and, most importantly, manageable scope. You simply can’t assess everything at once, so you have to be smart about your priorities.
First things first, get a complete inventory of your cloud footprint. This means figuring out which specific cloud assets, services from IaaS and PaaS to SaaS and data sets need your attention most urgently. Think about how critical each piece is to the business.
For instance, a customer-facing e-commerce app on AWS that handles sensitive payment data? That should be right at the top of your list. An internal development sandbox with zero production data, on the other hand, can probably wait. Documenting these priorities keeps your cloud risk assessment focused and ensures you get high-impact results from day one.
Assemble Your Cross-Functional “A-Team”
A cloud risk assessment should never be a solo mission run by the security department. To get the full picture—a true 360-degree view of your risks you absolutely must bring together a cross-functional team. When you only look at things from one angle, you’re guaranteed to have blind spots. Involving people from across the business also builds a culture where everyone feels responsible for security, which is critical for success in the long run.
Your ideal team should have people from a few key areas:
- IT and Cloud Operations: These are the folks on the ground. They understand the technical architecture, how things are configured, and the day-to-day reality of managing your cloud environment.
- Security: Your security experts bring their knowledge of threat modelling, vulnerability management, and how to navigate complex compliance rules.
- DevOps: Engineers from your DevOps team have priceless insights into the software development lifecycle, CI/CD pipelines, and all things automation.
- Legal and Compliance: This group makes sure your assessment lines up with legal duties like the DPDPA and other industry-specific standards.
- Business Leaders: Getting product owners or department heads involved is key. They help translate technical jargon into real-world business impact, like lost revenue or a damaged reputation.
This collaborative approach ensures that when you find a risk, you’re not just looking at its technical severity, but also at what it could actually cost the business.
A common mistake I see is treating a cloud risk assessment like a purely technical audit. Real success comes when you frame security risks in business terms. When a business leader understands how an unpatched server could directly derail their quarterly sales targets, they suddenly become your biggest ally in getting it fixed.
Choose the Right Framework for the Job
With your team assembled and your scope defined, you need a structured approach to guide the work. A good framework gives you a repeatable, organised process that stops your efforts from descending into chaos. It provides a common language for talking about risk and a clear roadmap for the evaluation.
There are several well-established frameworks you can adapt for a cloud risk assessment. The best one for you often depends on your industry, regulatory pressures, and how mature your organisation’s security programme is.
Common Framework Options:
- NIST Cybersecurity Framework (CSF): A very popular and flexible choice. It helps organisations manage risk through five core functions: Identify, Protect, Detect, Respond, and Recover.
- ISO/IEC 27005: This is an international standard specifically for information security risk management. It offers a more formal process for identifying, analysing, and treating risks.
- Cloud Security Alliance (CSA) Cloud Controls Matrix (CCM): As the name suggests, this is a framework built specifically for cloud computing. It maps its controls across numerous industry standards and regulations, which can be a huge time-saver.
In my experience, many organisations land on a hybrid approach. They’ll borrow elements from different frameworks to build a custom model that’s a perfect fit for their unique cloud environment and business needs. The goal isn’t to follow a framework rigidly; it’s to use it as a tool to make sure your cloud risk assessment is thorough, consistent, and truly comprehensive.
How to Identify and Categorise Cloud-Specific Risks

Now that you’ve done the prep work, the real investigation can begin. Uncovering risks in the cloud isn’t just a technical exercise; it’s a mix of deep-dive analysis and good old-fashioned detective work. You have to get your hands dirty, digging into configurations, running scans, and just as importantly talking to the people who build and manage your systems.
Think of this phase as a comprehensive health check-up. You’re combining the “lab tests” of automated scanning with the crucial “patient consultation” of interviewing your teams. The goal here is simple: build a complete, unfiltered list of every potential risk you can find.
Don’t jump the gun and start fixing things as you find them. That’s a classic mistake that can derail the whole process. Right now, your only job is discovery.
Uncovering Technical Vulnerabilities
Your first port of call is a thorough technical review. This is where you’ll combine automated tooling with manual checks to pinpoint weaknesses baked directly into your cloud infrastructure. Tools are fantastic for finding common problems at scale, but they’re most effective when guided by human expertise.
A solid starting point is always a deep dive into the configuration of your core cloud services. This is especially vital in Infrastructure as a Service (IaaS) and Platform as a Service (PaaS) environments like those on AWS, Azure, or Google Cloud.
Some of the usual suspects include:
- Identity and Access Management (IAM) Roles: Hunt for overly permissive roles. If you see a user or service with
*:*(all permissions on all resources), that’s a massive red flag that needs immediate attention. - Storage Configuration: Look for publicly accessible storage, like Amazon S3 buckets or Azure Blob Storage containers, that have no business being open to the world.
- Network Security Groups: Scrutinise your firewall rules. Are sensitive ports like RDP (3389) or SSH (22) open to the entire internet (
0.0.0.0/0)? - Exposed Secrets: This one is surprisingly common and incredibly dangerous. Scan your code repositories and configuration files for hardcoded API keys, database credentials, or other secrets.
This technical audit is the foundation of any good https://signiance.com/cloud-security-assessment/. To get a clearer picture of how these elements fit into the larger process, it’s worth understanding the full scope of a professional review.
Don’t just trust the “green checkmark” from your security tools. Context is king. A public S3 bucket might be perfectly fine if it’s hosting your website’s static assets. But that same configuration on a bucket filled with customer data is a critical incident waiting to happen.
Capturing Procedural and Operational Risks
Technology is only one part of the equation. The human element the processes and behaviours around your cloud environment is just as likely to create risk. This means you need to step away from the keyboard and talk to your teams.
Interviewing developers and DevOps engineers often uncovers risks that no scanner could ever find. Ask them to walk you through their deployment pipeline. How is code tested and promoted? How are infrastructure changes approved and rolled out? You might find that security checks are regularly skipped to meet tight deadlines, or that there’s no formal process for decommissioning old, unused cloud resources.
For instance, cloud security risks in India remain alarmingly high. Recent analysis revealed that nearly 29% of organisations are dealing with “toxic cloud trilogies” a dangerous combination of public-facing workloads, excessive permissions, and critical vulnerabilities. This is made worse by findings that over half of companies using AWS ECS have secrets exposed in insecure locations.
While these numbers are an improvement on previous years, they show just how much of a challenge this is for Indian enterprises. You can read more about these cloud security risk findings to better understand the regional threat landscape.
Creating a Meaningful Risk Categorisation System
Once you have a running list of issues, you need to bring some order to the chaos. Simply labelling risks as “high,” “medium,” or “low” isn’t enough. A more nuanced categorisation system gives you far greater clarity and helps you understand your threat landscape from a business perspective, not just a technical one.
A practical way to do this is to group risks by their source or domain. This simple step makes it much easier to assign ownership and track remediation down the line.
Here’s a look at some common categories you might encounter during an assessment.
Common Cloud Risk Categories and Examples
This table breaks down some of the most frequent risk types, along with real-world examples to help you spot them in your own environment.
| Risk Category | Description | Practical Example |
|---|---|---|
| Misconfiguration | Incorrect setup of cloud services that exposes the environment to threats. | An Amazon S3 bucket containing sensitive documents is configured for public read access. |
| Access Control | Weaknesses in how users and services are authenticated and authorised. | A developer is granted administrator-level access to the entire production account. |
| Data Exposure | Risks related to the security and privacy of data stored in the cloud. | Unencrypted backups of a customer database are stored in a development environment. |
| Compliance Risk | Failure to meet regulatory or industry standards (e.g., DPDPA, PCI-DSS). | Storing Indian customer data in a server located outside of the country’s jurisdiction. |
| Operational Risk | Threats to business continuity, such as outages or lack of redundancy. | A critical application is deployed in a single availability zone with no failover plan. |
By categorising risks this way, you move from a messy list to a structured inventory. This organised view is the foundation for the next crucial phase: analysing the potential impact and prioritising what to fix first.
Analysing Risks and Prioritising What Matters Most

So, you’ve done the discovery work and now have a list of potential cloud risks. That’s a great start, but it’s only half the job. A raw list of vulnerabilities can be completely overwhelming, often leading to a classic case of analysis paralysis where nothing gets done.
The real challenge and where the value lies is in sifting through that noise. We need to figure out what truly threatens the business. This is where we move past purely technical severity ratings and start thinking like business leaders. After all, a “critical” vulnerability on a temporary test server is just an annoyance. A “medium” vulnerability on your production database holding customer PII? That’s a potential catastrophe.
Bringing in the Risk Analysis Matrix
To bring some much-needed objectivity to this process, a risk analysis matrix is one of the best tools in the arsenal. It’s a simple but powerful way to visualise your risks by plotting them against two fundamental dimensions: likelihood (how probable is it?) and impact (how bad would it be?).
This visual grid immediately helps you categorise threats. You can quickly see what falls into the scary “High Impact, High Likelihood” corner, which naturally becomes your top priority.
Defining Business Impact Beyond Technical Jargon
This is a critical point: the “impact” score has to mean something to people outside of IT. If you can’t explain a risk in terms of business consequences, you’ll never get the buy-in or budget needed to fix it. This is where that cross-functional team you assembled earlier really proves its worth.
Work together to define what impact actually looks like for your organisation. It’s rarely just one thing.
Consider these areas:
- Financial Impact: Are we talking about direct monetary loss? This could be anything from regulatory fines under the DPDPA to lost sales from downtime or the sheer cost of the cleanup effort.
- Operational Impact: How badly would this mess up our daily work? Could a core application go offline, grinding a whole department to a halt?
- Reputational Impact: What would this do to our brand? A significant data breach can erode customer trust for years, with damage that far outstrips the initial financial hit.
- Compliance Impact: Does this risk push us into a state of non-compliance with laws or industry standards we’re bound to?
By scoring each risk on a scale (say, 1 to 5) across these different facets, you create a far more nuanced and realistic profile of the threat. An exposed API key might have a low initial financial cost, but if it leads to a massive data leak, the reputational and operational impact could be devastating.
Don’t make the classic mistake of trying to score these risks in a vacuum. Go to a product owner and ask them directly, “If this system went down for a day, what would that do to your quarterly targets?” When you frame the discussion this way, technical jargon melts away, and you’re left with tangible business consequences.
Calculating the Final Risk Score
With your impact and likelihood scores defined, you can now calculate a final risk rating. The most straightforward and widely used method is simple multiplication:
Risk Score = Impact x Likelihood
This formula gives you a number for each risk, making it incredibly easy to stack-rank your list from most to least urgent.
For instance, a risk with a catastrophic Impact score of 5 and a Likelihood of 4 (likely) gets a Risk Score of 20. Meanwhile, a different risk with a minor Impact of 2 but a very high Likelihood of 5 only scores 10.
The maths instantly clarifies that the first risk is twice as important to fix, even though the second one is technically more likely to occur. This prioritised list is the ultimate goal of your analysis. It’s your action plan, ensuring your team dedicates its finite time and resources to tackling the threats that genuinely matter.
Building Your Cloud Risk Mitigation Strategy
A detailed cloud risk assessment is an excellent diagnostic, but its real value comes from what you do next. Identifying the risks is just the first step. The real work and where you build genuine resilience is turning that knowledge into a concrete mitigation strategy. It’s about moving from a list of potential problems to a clear, actionable plan that actively strengthens your security posture.
Once you have your prioritised list of risks, every single one needs a response. You’ve got to decide whether to mitigate, transfer, accept, or avoid it. This decision-making process is the absolute core of effective risk management.
Choosing Your Risk Response
Not all risks are created equal, so you can’t treat them all the same way. Picking the right response is a balancing act. You have to weigh the risk’s potential impact against the cost of fixing it and your organisation’s overall appetite for risk.
This is where you need to make a strategic call. Each identified risk demands a clear plan of action, and you generally have four paths to choose from.
Here’s a quick comparison of the main strategies you’ll be deciding between.
Risk Response Strategy Comparison
| Strategy | Action | When to Use It | Example |
|---|---|---|---|
| Mitigate | Implement controls to reduce the risk’s likelihood or impact. | For high-impact, high-likelihood risks that are core to your operations. This is your most common response. | Enforcing Multi-Factor Authentication (MFA) to address weak access controls. |
| Transfer | Shift the financial burden of the risk to a third party. | When the risk is significant but more cost-effective to insure against than to mitigate internally. | Purchasing a cyber insurance policy to cover potential costs from a data breach. |
| Accept | Formally acknowledge the risk and choose not to take action. | For low-impact, low-likelihood risks where the cost of mitigation is higher than the potential damage. | A minor compliance gap in a non-critical, internal-only application. |
| Avoid | Discontinue the activity or process that creates the risk. | For catastrophic risks that cannot be effectively mitigated or transferred. | Decommissioning a legacy application that can’t be secured or deciding against a cloud service with poor security standards. |
Making a conscious, documented choice for every single risk is what matters most. Don’t fall into the trap of just ignoring something.
Formally accepting a risk is not the same as ignoring it. A documented acceptance proves you’ve done your due diligence and made a strategic business decision.
Integrating Security into DevOps
For the risks you decide to mitigate, weaving security directly into your development and operations pipeline what we call DevSecOps is a total game-changer. Instead of security being a final hurdle, you embed automated checks and controls throughout the entire software lifecycle. This “shift-left” philosophy catches vulnerabilities much earlier, making them faster, cheaper, and far easier to fix.
Automation is especially powerful in a dynamic cloud environment. Frankly, the difference between manual and automated approaches is night and day.
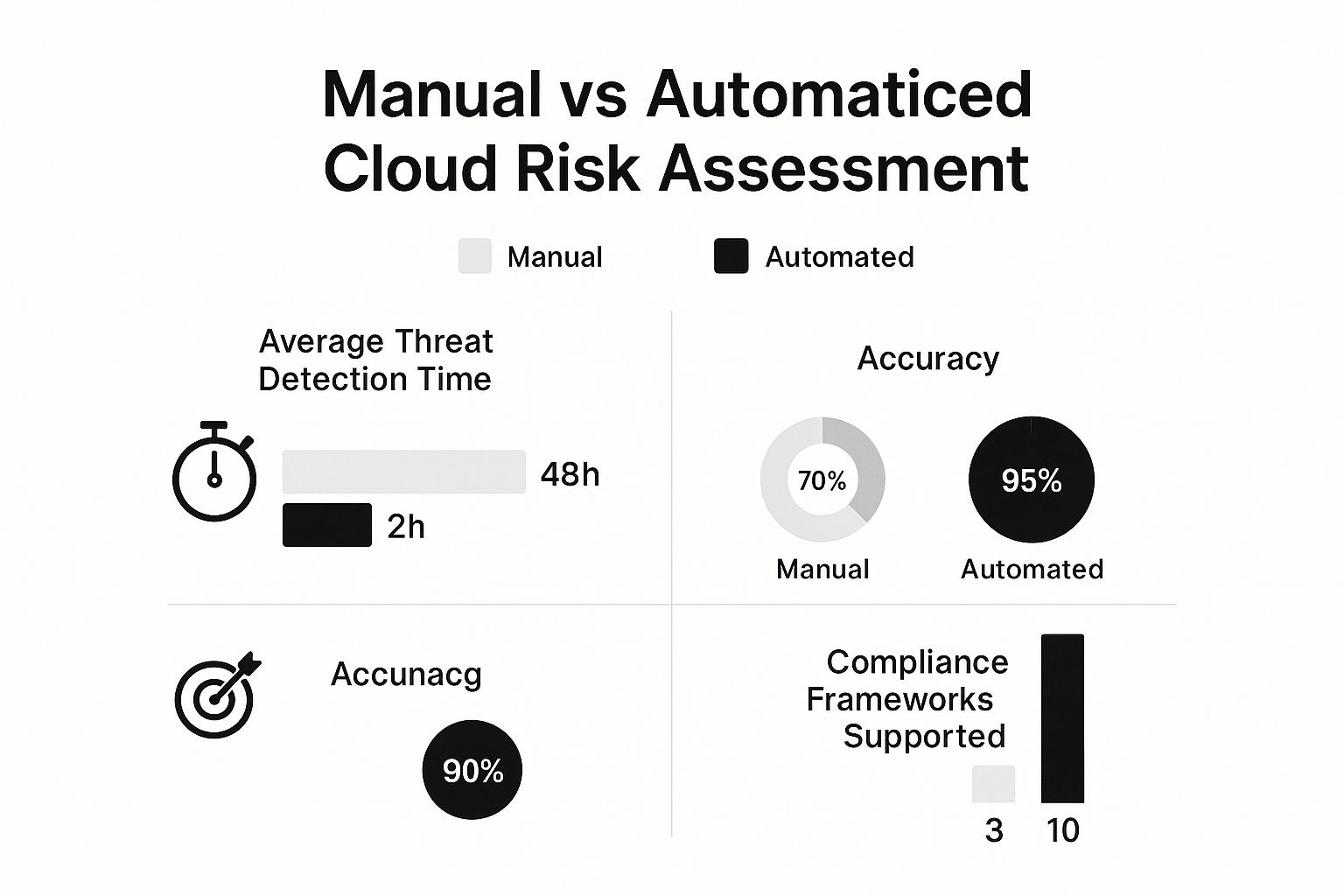
The data here really speaks for itself. Automation can slash threat detection times from days down to hours while dramatically improving accuracy.
This kind of investment in security automation and cloud-native tools is becoming a major priority for Indian businesses. In fact, end-user spending on information security in India is projected to reach $3.3 billion in 2025, which is a massive 16.4% jump from 2024. You can read more on Gartner’s information security spending forecast for the full breakdown. This surge is all about managing threats from new tech and complex regulations, with a heavy focus on cloud security and access management.
This isn’t just about spending more money; it’s a strategic shift. By building security into your core processes, you stop just plugging individual holes and start creating a system that is secure by design. This approach slots perfectly into established frameworks for operational excellence. You can explore our guide on the cloud adoption framework to see how these principles tie into a bigger, more robust strategy.
Common Questions About Cloud Risk Assessment
Even with the best-laid plans, getting into the nitty-gritty of a cloud risk assessment almost always brings up a few questions. That’s perfectly normal. After all, you’re dealing with a complex mix of technology, processes, and business logic, so it’s smart to be prepared for the common sticking points.
Tackling these questions head-on is the best way to demystify the process for everyone involved, from your technical team to key stakeholders. Let’s walk through some of the queries I hear most often from organisations undertaking this critical exercise.
How Often Should We Conduct a Cloud Risk Assessment?
This is easily the most frequent question, and the answer isn’t as simple as “once a year.” The right frequency really hinges on how dynamic your cloud environment is. For most organisations, a full, comprehensive assessment on an annual basis is a solid starting point.
But the cloud is anything but static, and your risk management can’t be either. You should trigger a new or updated cloud risk assessment anytime a significant change happens. Think of events like:
- Major Cloud Migrations: Moving a core application or database to the cloud is a huge shift, introducing entirely new variables that need to be assessed right away. If you’re planning a move, our guide on cloud migration best practices offers a great framework.
- Launching New Services: When you’re about to roll out a new customer-facing app or a critical internal system, it deserves its own focused assessment.
- Adopting New Technologies: Bringing in new tools like serverless functions or AI/ML platforms means new attack surfaces and potential blind spots.
- Significant Architectural Changes: If you re-architect a major part of your infrastructure, you’ve likely changed data flows and security controls, which calls for a fresh look.
Here’s how I like to think about it: your big annual assessment is like a thorough physical. The event-driven assessments are like going to the doctor for a specific issue that crops up between your check-ups. Both are essential for staying healthy.
“A cloud risk assessment is not a one-and-done event; it’s a continuous cycle. Your cloud environment is constantly evolving, with new services being deployed and configurations changing daily. Your risk management process must be just as agile to keep pace.”
Is This Just for Public Cloud Environments?
Absolutely not. While giants like AWS, Azure, and Google Cloud dominate the conversation, the fundamental principles of a cloud risk assessment are universal and apply to any cloud model you’re using.
This absolutely includes:
- Private Cloud: Just because the hardware is dedicated to you doesn’t make it immune. You still face risks from misconfigurations, insider threats, and software vulnerabilities.
- Hybrid Cloud: These setups can be incredibly complex. With data and workloads moving between your on-premise data centres and the public cloud, an assessment is the only way to ensure security and compliance across the board.
- Multi-Cloud: Juggling multiple cloud providers often leads to security silos and inconsistent policy enforcement. A single, holistic assessment is crucial for getting a unified view of your actual risk posture.
The core process identifying what’s valuable, figuring out what could go wrong, and prioritising those risks is the same no matter where your infrastructure lives. The specific threats and controls might change, but the need for a structured assessment never does.
How Do We Justify the Cost and Effort to Leadership?
Getting the green light for a cloud risk assessment often comes down to one thing: translating technical risk into business impact. Your leadership team needs to see the return on this investment, and that return isn’t always as clear as a sales figure.
The trick is to avoid framing it as a technical chore or just another “cost of doing business.” Instead, you need to present it as a strategic investment that enables resilience and growth. I’ve found it’s best to build your case around a few key pillars that resonate with business goals.
Building Your Business Case:
- Risk Reduction: Put a number on it. Use industry data to show the average cost of a breach and connect it to specific risks you know exist. For instance, “A breach of our customer database could expose us to ₹X crore in fines under the DPDPA, plus the immense reputational damage.”
- Operational Efficiency: A good assessment often uncovers more than just security gaps. It frequently highlights over-provisioned resources or inefficient setups, which can lead to direct, tangible savings on your monthly cloud bill.
- Enabling Innovation: When the business feels confident in its cloud security, it can move faster. You can frame the assessment as the project that “clears the path” for adopting new tech and launching new services without fear.
- Maintaining Customer Trust: In today’s market, security is a powerful differentiator. Show how a proactive security posture helps keep the customers you have and win the ones you want.
By shifting the conversation to financial risk, cost savings, and business enablement, a cloud risk assessment stops looking like a necessary evil and starts looking like the powerful business tool it truly is. That strategic alignment is how you get the buy-in you need.
Ready to move beyond questions and build a truly resilient cloud infrastructure? At Signiance Technologies, we provide expert cloud risk assessments that turn findings into actionable, business-focused security strategies. We help you protect your assets, ensure compliance, and innovate with confidence. Learn how we can secure your cloud journey.
