Mastering Cloud Security Architecture Fundamentals
A cloud security architecture diagram isn't just a simple network sketch; it's the blueprint for your entire cloud defense strategy. It visually represents your security posture, outlining the interaction of various components and the placement of your safeguards. This clarity is essential for preventing breaches by identifying potential vulnerabilities before exploitation. A well-designed diagram can be the crucial difference between a secure system and a compromised one.
These diagrams are also vital for effective collaboration. Imagine explaining your complex security setup to a new team member or an external auditor without a clear visual aid. A cloud security architecture diagram provides a common language, ensuring everyone understands the system. This shared understanding leads to faster incident response and smoother teamwork. For further information on cloud security assessments, check out this helpful resource: How to master your cloud security assessment.
Regulatory compliance also significantly influences these diagrams. Recent regulatory and technological advancements in India, such as the Digital Personal Data Protection Act 2023 (DPDPA) and updates to the National Cybersecurity Strategy, mandate stricter data privacy and security requirements. Consequently, cloud security architecture diagrams now must explicitly represent data flow, encryption zones, and access control policies to ensure compliance. For more insights into relevant cloud security statistics, see: Cloud Security Statistics.
Key Components of a Cloud Security Architecture Diagram
A comprehensive diagram requires more than just basic shapes and lines. It needs to accurately represent the core elements contributing to your overall security. Here are some essential components:
-
Identity and Access Management (IAM): Clearly define user roles, permissions, and access control policies to control resource access effectively.
-
Network Security: Illustrate your virtual private clouds (VPCs), firewalls, intrusion detection systems, and other network security measures.
-
Data Security: Show how data is encrypted, both in transit and at rest, and highlight data loss prevention mechanisms and access control policies.
-
Security Monitoring and Incident Response: Include your security information and event management (SIEM) system, logging processes, and incident response plan.
Clarity Over Complexity
While including all essential components is crucial, maintaining clarity is paramount. An overly cluttered diagram is just as unhelpful as a missing one. Think of it like a map: a good map provides necessary information without overwhelming the user. The goal is to create a diagram easily understood by all stakeholders, from technical experts to business leaders. This requires clear labels, consistent icons, and a logical layout.
By focusing on these fundamentals, you can create a cloud security architecture diagram that's both visually appealing and a powerful tool for strengthening your security posture and achieving compliance.
Essential Elements That Make Diagrams Actually Useful
Cloud security architecture diagrams are more than just simple visuals. They are crucial tools for understanding and managing your security posture. A well-constructed diagram allows for faster incident response, clearer communication, and stronger overall security. The following infographic shows how core cloud service components connect within a simplified workspace:
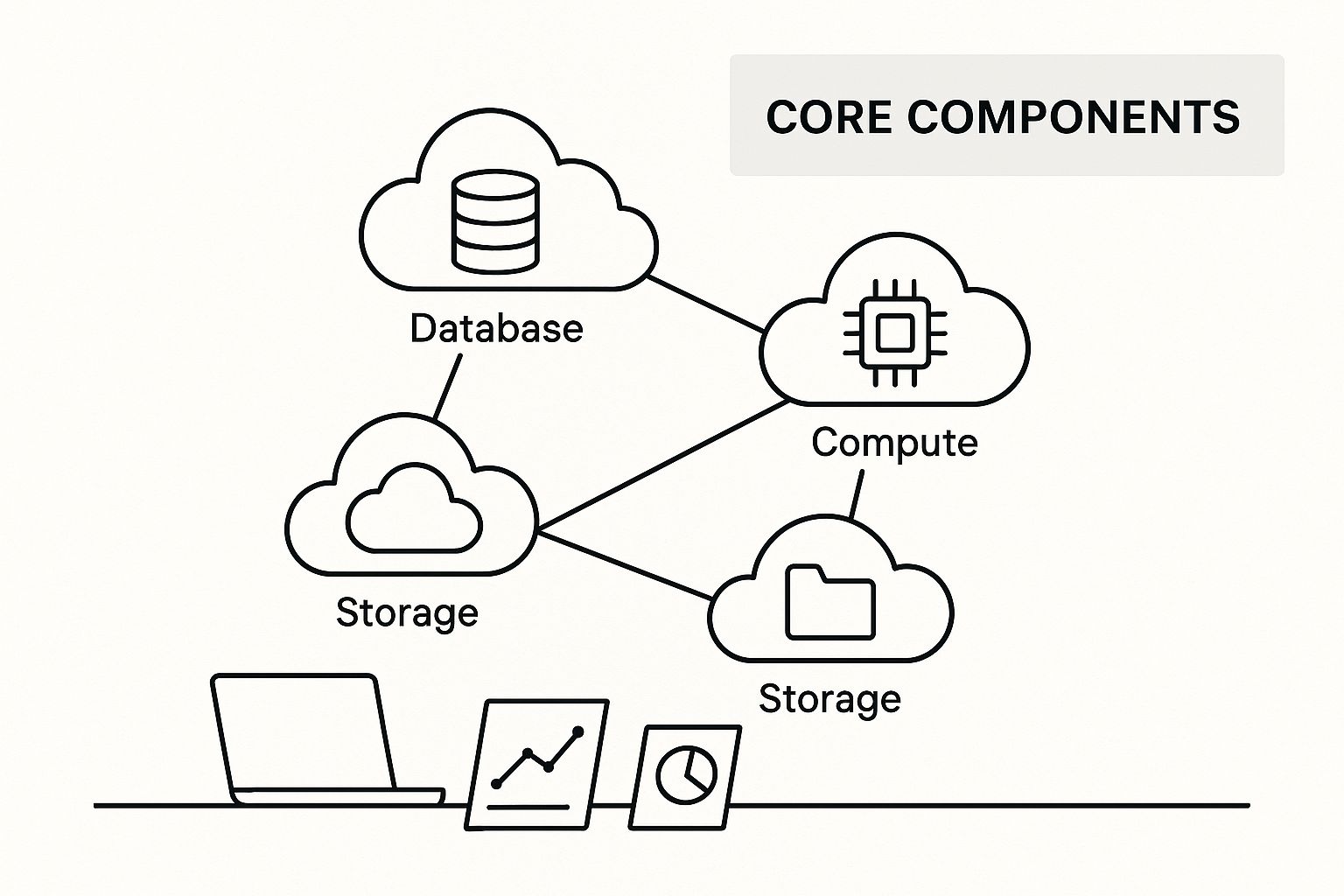
As shown, each component represents a vital part of cloud security, highlighting the need for an integrated approach to achieve robust protection. This interconnectedness emphasizes how important it is to visualize the relationships between these components to ensure comprehensive security. But what transforms a cloud security architecture diagram from a basic visual into a strategic asset? Let's explore the key elements.
Defining Security Boundaries
Clearly defined security boundaries are paramount. This involves visually separating different environments, such as production, development, and testing environments. Think of it like zoning regulations: different zones have different rules. Your cloud environments also need different security levels. With the increased use of multi-cloud strategies, clearly showing the boundaries between different cloud providers like AWS or Azure is also critical.
Visualizing Access Controls
Your diagram should effectively represent access controls. This includes showing user roles, permissions, and how these affect access to different resources. A database administrator should have different access privileges than a member of the marketing team. Visualizing these controls helps prevent unauthorized access and ensures compliance with regulations like the GDPR.
Highlighting Data Classification Levels
Data classification is essential. Your diagram should illustrate how data is categorized based on its sensitivity. This might include classifications like "confidential," "restricted," and "public." Visually representing these classifications helps teams quickly grasp the required security measures for each data type.
To understand how these core components contribute to a robust security architecture, let’s analyze their individual functions and impact.
| Component | Security Function | Compliance Impact | Implementation Priority |
|---|---|---|---|
| Security Boundaries | Isolation of environments, preventing unauthorized access between them | Supports compliance by restricting data flow and access based on sensitivity and regulatory requirements | High |
| Access Controls | Management of user permissions and roles, limiting access to resources | Directly impacts compliance by enforcing least privilege and data access restrictions | High |
| Data Classification | Categorization of data based on sensitivity, enabling appropriate security measures | Enables compliance by ensuring sensitive data is handled according to regulations | High |
| Hybrid Infrastructure Integration | Secure connection and management of on-premise and cloud resources | Facilitates compliance by extending security policies and controls across both environments | Medium |
| Incident Response Plan Integration | Visual representation of incident response workflows, accelerating response times | Supports compliance by enabling faster identification and remediation of security breaches | Medium |
This table summarizes the crucial roles each component plays in maintaining a strong security posture and adhering to compliance standards. Prioritizing the implementation of these components is vital for a robust and compliant cloud security architecture.
Incorporating Hybrid Infrastructures
Many organizations utilize hybrid infrastructures incorporating both on-premise and cloud components. Representing this hybridity within your cloud security architecture diagram is key. This means showing the connections between on-premise systems and cloud resources, along with the security measures in place across both environments. This provides a holistic security overview, ensuring no gaps exist between your physical and cloud infrastructure.
Enhancing Incident Response
During security incidents, a well-designed diagram becomes an invaluable tool. It enables teams to quickly identify affected areas, understand dependencies, and take appropriate action. By including elements like monitoring systems (Datadog) and incident response workflows directly in the diagram, you can significantly improve response times and minimize potential damage.
Building Architecture That Anticipates Real Threats
Creating effective cloud security architecture diagrams goes beyond simply documenting your current infrastructure. It requires a forward-thinking approach, anticipating potential future threats and vulnerabilities. Instead of reacting to security breaches after they occur, proactive planning and design of defensive layers are essential for robust cloud security. Security experts achieve this by incorporating threat modeling into their visual design process. This involves systematically analyzing potential attack vectors based on the specific architecture of your cloud environment. Essentially, it requires thinking like a potential attacker and identifying how they might attempt to breach the system.

Identifying Attack Vectors Through Architectural Analysis
A practical approach to identifying these attack vectors involves conducting a thorough architectural review. This means meticulously examining every component within your cloud security architecture diagram. This review should encompass everything from the network perimeter to individual virtual machines. For example, are there any exposed APIs that could be exploited? Are your security groups configured correctly? This analysis helps pinpoint vulnerabilities that might otherwise be overlooked.
This detailed review also allows for the prioritization of defensive efforts. By focusing on areas of greatest risk, resources can be allocated effectively. It's important to remember that threat modeling isn't a one-time task. It should be an ongoing process, continuously evolving alongside changes in your architecture and the emergence of new threats.
Positioning Defensive Layers That Work Together
Effective cloud security necessitates a multi-layered approach. This involves integrating various security controls, including firewalls, intrusion detection systems, and access control mechanisms. The strategic placement of these layers within the architecture is crucial for maximizing their effectiveness. For instance, a web application firewall (WAF) placed in front of web servers provides protection against common web attacks.
This layered approach creates a robust defense capable of withstanding a range of threats. It also allows for the implementation of "defense in depth." This principle ensures that even if one security layer is compromised, other layers remain in place to prevent a complete breach.
Incorporating Monitoring and Response Mechanisms
Your cloud security architecture diagram should also incorporate monitoring systems and automated defenses. These include tools for detecting malicious activity, alerting security teams, and automatically responding to incidents. This system acts as a security alarm for your cloud environment. Monitoring tools serve as sensors, alerting systems act as the control panel, and automated responses, such as shutting down a compromised server, mitigate damage. This real-time visibility is essential for preventing incidents from escalating into significant breaches. Learning best practices from incident response experts can be incredibly valuable.
For more insights into the growing importance of cloud security, consider the Indian market. Explore the Indian Cloud Security Market. This market is projected to experience significant growth, with a CAGR of nearly 29.88% for cloud security solutions between 2025 and 2029. In 2024 alone, India reported 369.01 million malware detections, highlighting the critical need for robust security architecture.
Testing and Adapting to the Evolving Threat Landscape
Finally, your cloud security architecture diagram should be continuously tested and adapted. This involves regular security assessments, penetration testing, and vulnerability scans. This continuous improvement cycle ensures that weaknesses are identified and addressed before they can be exploited. As new technologies emerge and best practices evolve, your architecture diagram should be updated accordingly. This dynamic approach ensures that your cloud security architecture remains effective against ever-changing threats.
Designing For Compliance Without Losing Flexibility
Maintaining a flexible cloud architecture while navigating the complexities of regulatory compliance can be a difficult balancing act. It requires careful consideration of how various compliance frameworks, such as the DPDPA in India, impact the design of your cloud security architecture diagram. Understanding what visual elements auditors expect is also essential. This section will provide guidance on designing a cloud architecture that is both compliant and adaptable. For further information, you might be interested in this resource: How to master compliance automation.
Incorporating Audit Trails, Data Sovereignty, and Access Logging
Real-world scenarios highlight the critical importance of incorporating audit trails, data sovereignty controls, and access logging mechanisms into your cloud security architecture diagrams. These elements provide a transparent record of all activities within your cloud environment. They also demonstrate adherence to data location regulations and offer a detailed log of who accessed specific resources and when. By visually integrating these features into your diagrams, meeting multiple regulatory standards concurrently becomes more manageable.
Data sovereignty, for instance, requires careful consideration. Your diagram should clearly illustrate where data is stored and processed to ensure compliance with regulations like the DPDPA. This visual representation significantly strengthens your compliance posture and simplifies the audit process.
Visual Documentation and Regulatory Adherence
Effective strategies exist for visually documenting compliance controls and designing an architecture that clearly demonstrates regulatory adherence without negatively impacting performance. For example, color-coding different security zones based on their specific compliance requirements can offer a concise overview of your security posture.
Using standardized icons for security components, such as firewalls or intrusion detection systems, can further enhance clarity and understanding. This visual documentation makes demonstrating your compliance status a straightforward process.
Mapping Business Requirements to Technical Specifications
A crucial aspect of compliance is effectively mapping business requirements to technical specifications that consistently meet audit standards. This involves translating high-level business objectives, like protecting sensitive customer data, into concrete technical implementations, such as encrypting data at rest and in transit.
This alignment ensures your technical implementation directly supports your business needs while simultaneously fulfilling regulatory requirements. This mapping should be clearly represented in your cloud security architecture diagram, illustrating how technical specifications satisfy both business needs and regulatory mandates. This approach streamlines audits and bolsters your overall security posture.
Tools And Workflows That Actually Work
Transforming your theoretical cloud security architecture knowledge into practical, maintainable documentation requires the right tools and workflows. This means finding platforms that help create cloud security architecture diagrams that are not just created once, but actively used and updated by security teams. You might be interested in: How to master your cloud adoption framework.

Collaborative Development and Governance
Collaboration is essential for building accurate diagrams. This includes fostering communication between technical teams to ensure a shared understanding of the architecture.
Establishing clear governance processes is also crucial for keeping diagrams up-to-date as cloud environments change. Think of your documentation like a living document requiring regular updates to stay relevant. This means implementing version control procedures, much like you would with software code, and ensuring updates reflect infrastructure changes.
Practical Workflows for Long-Term Success
Creating templates for common architectural patterns can save time and ensure consistency. It's similar to building with pre-fabricated components—the process is streamlined, and uniformity is ensured.
Establishing diagram standards within your organization is also beneficial. These standards might include conventions for icons, color schemes, and labeling. This consistency makes it easier for everyone to understand and use the diagrams, contributing to long-term architectural success.
Leading Tools and Real-World Performance
Several tools are excellent for creating and managing cloud security architecture diagrams. Each tool addresses different needs and provides various features. Choosing the right tool depends on factors like your organization's size, your architecture's complexity, and your budget.
To help you evaluate these tools, we've compiled a comparison table highlighting their key features, ideal use cases, pricing, and collaboration capabilities.
The following table, "Cloud Security Architecture Tools Comparison," provides a comprehensive comparison of leading tools for creating and managing security architecture diagrams.
| Tool | Key Features | Best Use Case | Pricing Model | Collaboration Features |
|---|---|---|---|---|
| Lucidchart | Visio import, extensive shape libraries, real-time collaboration | Teams needing intuitive diagramming with strong collaborative features | Subscription-based | Real-time co-editing, commenting, version history |
| Draw.io | Open source, free version available, integrations with other platforms | Cost-conscious teams or those preferring open-source solutions | Freemium | Real-time collaboration, version history |
| Microsoft Visio | Extensive stencil library, integration with other Microsoft products | Organizations heavily reliant on the Microsoft ecosystem | Subscription or one-time purchase | Co-authoring, commenting |
| Cloudcraft | Automated AWS diagram generation, cost estimation | Visualizing AWS environments and understanding costs | Subscription-based | Sharing and collaboration features within teams |
This comparison allows organizations to select the best tool for their specific needs and budget. It's crucial to get honest reviews of these tools and how they perform in real-world enterprise environments. This includes understanding their limitations and learning from other organizations' experiences. This information can help you make informed decisions and avoid potential problems.
By implementing effective workflows, using the right tools, and prioritizing collaboration, you can create dynamic cloud security architecture diagrams that actively contribute to a stronger overall security posture.
Measuring Success And Continuous Improvement
Excellence in cloud security architecture isn't a final destination, but an ongoing process. It requires constant validation and refinement, much like a ship needing continuous course correction to stay on track. This means establishing metrics to prove the effectiveness of your cloud security architecture diagram and finding areas for improvement before issues arise. Your security architecture must adapt to the ever-shifting conditions of the digital realm.
Establishing Metrics for Architectural Effectiveness
How can you tell if your architectural approach is truly working? The answer lies in establishing clear Key Performance Indicators (KPIs). These metrics should align with your organization's overall security goals. For example, a key metric could be the reduction in successful security breaches.
Other valuable metrics include the time it takes to identify and fix vulnerabilities, or the number of systems adhering to security policies. By monitoring these metrics over time, you gain valuable insights into the effectiveness of your cloud security architecture diagram.
Creating Feedback Loops for Continuous Improvement
Feedback loops are essential for integrating lessons learned from various sources, such as security incidents, audit findings, and operational hurdles. These insights should be used to refine your cloud security architecture diagram.
For instance, if an incident reveals a flaw in your access control, your diagram should be updated to reflect the necessary improvements. Similarly, audit feedback can highlight compliance gaps requiring immediate attention. This iterative process ensures your architecture is constantly evolving and strengthening.
One significant trend in cloud security architecture, particularly in India, is the rapid increase in investments and technology adoption. By 2025, India's information security market is predicted to hit $3.3 billion. This is fueled by a projected 16.4% rise in end-user spending compared to 2024. Gartner provides a more in-depth analysis.
Security services, which are often incorporated into cloud security architectures, are expected to see the most significant growth among all security segments, with a 19% increase anticipated in 2025. This growth emphasizes the importance of a robust and adaptable cloud security architecture.
Keeping Architecture Current With Business and Technological Changes
Your cloud security architecture diagram should not exist in isolation. It must align with the evolving needs of your business and keep pace with emerging technologies. As your organization adopts new cloud services or ventures into new markets, your diagram should mirror these changes.
Staying informed about new security threats and best practices is also vital. Just as a doctor keeps up with medical advancements, security architects must remain current with the constantly evolving security landscape. This proactive approach ensures your architecture stays relevant and effective.
Team Training and Architectural Governance
Practical training for teams on diagram interpretation, along with establishing sound architectural governance, is paramount. This includes clear documentation and training sessions that explain how to interpret your cloud security architecture diagram. Think of it like teaching someone how to read a complex map – it requires clear guidance and explanation.
Establishing clear architectural governance processes further bolsters your organization’s long-term security goals while maintaining operational flexibility. This means clearly defined roles and responsibilities for managing and updating the diagram. It also involves establishing processes for approving changes to maintain architectural integrity. This structured approach promotes consistent security practices and allows your organization to react efficiently to changes.
Key Takeaways
Your journey to robust cloud security starts with a well-defined cloud security architecture diagram. This diagram isn't just a visual; it's your roadmap to a secure and compliant cloud environment. This section distills key insights into practical steps you can implement today, no matter your current architectural maturity.
Building a Diagram That Works
Define your security boundaries. Think of them like zoning regulations, each area having its own set of rules. Visually separating your production, development, and testing environments, as well as any multi-cloud boundaries, is critical. This clear separation prevents unauthorized access between environments and supports compliance by controlling data flow. Also, ensure your diagram clearly shows access controls, illustrating user roles, permissions, and their impact on resource access. This visualization helps enforce least privilege and restricts data access according to regulations, like those stipulated by the DPDPA in India.
Prioritizing Security Components
Implementing key security components is crucial for a robust architecture. Here's what to focus on:
-
Security Boundaries: Create clear boundaries between different environments to prevent unauthorized access.
-
Access Controls: Implement and visualize user permissions to manage resource access effectively.
-
Data Classification: Categorize data based on its sensitivity to apply the right security measures.
-
Hybrid Infrastructure: Securely connect and manage both on-premise and cloud resources to extend security policies across all environments.
-
Incident Response: Integrate your incident response workflows to enable faster identification and remediation of security breaches.
These components are the building blocks for a strong security posture and adhering to compliance standards.
Threat Modeling and Compliance
Building an architecture that anticipates threats is essential. Integrating threat modeling into your design process means thinking like an attacker. By identifying potential attack vectors through architectural analysis and strategically placing defensive layers like firewalls) and intrusion detection systems, you build a robust defense. For instance, analyze any exposed APIs for potential exploits and verify the correct configuration of your security groups.
Designing for compliance means incorporating audit trails, data sovereignty controls, and access logging mechanisms. These features not only demonstrate regulatory adherence but also enable efficient data management and improve the transparency of actions within your cloud environment. They strengthen your compliance position by providing auditable records of data access and system activities.
Tools and Continuous Improvement
Using the right tools and workflows can turn your theoretical knowledge into practical documentation. Select tools based on your organization’s needs and invest in training your team on diagram interpretation. Establishing clear architectural governance, including version control and diagram standards, ensures long-term maintainability and usability. This structured approach ensures your diagrams stay up-to-date and relevant, promoting consistent security practices.
Measuring success means using metrics like the reduction in security breaches and the time taken to resolve vulnerabilities. These metrics provide a concrete measure of your security posture's effectiveness. Create feedback loops to incorporate lessons learned from security incidents and audits. Just as a ship needs continuous course correction, your cloud security architecture requires ongoing adjustments. This continuous refinement ensures your architecture is constantly adapting and improving.
Ready to improve your cloud security? Explore Signiance Technologies’ comprehensive cloud solutions and build a resilient and secure cloud architecture.
