Think of cloud security monitoring as your dedicated, round-the-clock digital watchtower. It’s a system that keeps a constant eye on your entire cloud environment, actively looking for threats, vulnerabilities, and any risky settings that could leave you exposed. This isn’t just about defence; it’s about shifting your entire security mindset from reactive to proactive, neutralising problems long before they escalate into a full-blown crisis.
Why Cloud Security Monitoring Is Not Optional

Picture your cloud environment as a bustling digital city, home to your most valuable business assets. Would you leave that city completely unguarded? Of course not. Operating in the cloud without constant surveillance is exactly that—a gamble no modern business can afford to take. As more companies move their core operations online, robust cloud security monitoring stops being a “nice-to-have” and becomes an absolute business necessity.
This is far more than just a technical chore; it’s a fundamental part of managing business risk. Without a clear, real-time picture of your security health, you’re essentially flying blind. Good monitoring gives you the visibility you need to protect sensitive data, keep your operations running smoothly, and maintain the trust you’ve built with your customers.
To truly understand its importance, let’s look at the key objectives a solid monitoring strategy helps you achieve. The following table breaks down these primary business and security goals.
Key Objectives of Cloud Security Monitoring
| Objective | Description |
|---|---|
| Early Threat Detection | Identify and respond to suspicious activities in real-time, such as unauthorised access attempts or unusual data transfers, before they can cause damage. |
| Continuous Compliance | Automatically check cloud configurations against industry standards like GDPR, HIPAA, or PCI DSS to ensure you’re always compliant and avoid heavy fines. |
| Vulnerability Management | Proactively discover and flag security weaknesses, like unpatched systems or open ports, so they can be fixed before an attacker exploits them. |
| Incident Response | Provide detailed logs and context during a security event, which drastically speeds up investigation and remediation efforts for your security team. |
| Operational Visibility | Gain a comprehensive view of all activities happening across your cloud assets, helping to enforce security policies and detect insider threats. |
As you can see, these objectives go beyond simple security checks. They directly support business continuity, risk management, and regulatory adherence, making monitoring a core pillar of a healthy cloud strategy.
The Shift from Reactive to Proactive Defence
For a long time, security teams were stuck in a reactive loop, scrambling to clean up the mess after a breach had already happened. This “after-the-fact” approach simply doesn’t work in the cloud, where entire systems can be created and destroyed in minutes.
A proactive security stance, powered by continuous monitoring, lets you spot and fix potential threats before they’re ever exploited. It’s the difference between patching a hole in your ship after you’ve started taking on water and inspecting the hull for weak spots before you even set sail.
This forward-thinking approach is critical for a few key reasons:
- Spotting Threats Early: Catch suspicious behaviour as it happens, like strange API calls or someone trying to access an account they shouldn’t.
- Managing Vulnerabilities: Find weaknesses in your setup think unpatched software or exposed network ports before attackers do.
- Staying Compliant: Ensure your configurations consistently meet regulatory rules like PCI DSS, HIPAA, or GDPR, helping you sidestep costly penalties.
A Critical Investment in Business Resilience
Putting money into security is no longer just an IT budget line item; it’s a strategic business decision. The financial and reputational damage from a single cloud breach can be devastating. In India, for example, this growing awareness is fuelling major investment. Projections show that spending on information security in India is expected to hit $3.3 billion in 2025, a 16.4% jump from the year before. This rise is driven by relentless threats like ransomware and new data privacy regulations.
This trend underscores a global truth: effective cloud security monitoring is a direct investment in your business’s ability to withstand and recover from attacks. By keeping a vigilant watch over your digital turf, you’re not just defending against hackers. You’re also protecting against internal mistakes and misconfigurations, which are a surprisingly common cause of security incidents. Ultimately, it delivers the peace of mind that comes from knowing your most critical assets are properly protected, 24/7.
Uncovering Your Biggest Cloud Security Blind Spots
We often picture security breaches as elaborate, Hollywood-style cyberattacks. The reality, however, is usually much less dramatic and far closer to home. The most dangerous threats lurking in your cloud environment are frequently born from simple internal oversights the kind of human errors and misconfigurations that essentially leave the front door wide open. These are your biggest security blind spots.
Think about it like this: you can install the most sophisticated alarm system money can buy, but it’s completely useless if someone forgets to lock the door on their way out. In the cloud, that “unlocked door” could be anything from a publicly exposed storage bucket to an overly generous access policy or even an old, forgotten account with powerful privileges. These aren’t malicious acts, just small mistakes that create massive vulnerabilities.
Even with a full suite of top-tier security tools, if you aren’t constantly watching for these fundamental errors, you’re undermining your entire defence. Attackers actively seek out this low-hanging fruit because it provides the path of least resistance into your network.
The Pervasive Threat of Misconfigurations
Misconfigurations are dangerously common for a simple reason: cloud environments are incredibly complex and always in flux. A developer might open a port for a quick test and forget to close it. A new team member might be granted far more access than they actually need for their role. On their own, these seem like minor issues, but they pile up over time, creating a security posture full of holes.
Some of the most common and critical blind spots we see include:
- Publicly Exposed Storage Buckets: Accidentally setting a storage container, like an AWS S3 bucket, to be public. This can instantly expose sensitive customer data, company secrets, or login credentials to the entire internet.
- Overly Permissive IAM Roles: Giving users or services “administrator” or “root” access when they only need very specific permissions to do their jobs. If that one account gets compromised, the attacker has the keys to the kingdom.
- Unused or Dormant Credentials: Accounts from former employees or old service credentials that were never deactivated. These become ticking time bombs, just waiting for an attacker to discover and exploit them.
- Disabled Logging or Monitoring: Switching off services like AWS CloudTrail or Azure Monitor to cut costs. This is like trying to guard a building with a blindfold on, making it impossible to see who’s coming and going.
The scale of this problem is genuinely staggering. Research shows that cloud security risks, especially in regions like India, are overwhelmingly driven by customer error. It’s predicted that by 2025, a shocking 99% of cloud failures will be the customer’s fault, with misconfigurations already accounting for nearly 23% of all cloud security incidents today. These aren’t just hypotheticals; about 27% of businesses have reported public cloud breaches that were traced directly back to these kinds of errors.
Why Automation Is the Only Solution
In a dynamic cloud architecture where new resources are created and destroyed in minutes, trying to keep up with manual checks is a losing battle. It’s simply not possible for any human team. This is where automated cloud security monitoring becomes non-negotiable.
Automated monitoring is your tireless security guard, working 24/7 to scan your entire environment. It doesn’t get tired, it never takes a coffee break, and it won’t forget to check every single resource against your security rules.
This constant, automated vigilance is the only practical way to find and fix these blind spots across a sprawling, multi-cloud setup. A well-configured monitoring system can instantly flag a newly created public storage bucket or an access key that hasn’t been touched in 90 days, giving your team a chance to fix the problem before it’s exploited.
Without this level of automation, you’re always playing catch-up, reacting to breaches instead of preventing them. The first step is to understand where you currently stand, which is why a comprehensive cloud security assessment is so crucial. By systematically shining a light on these hidden risks, you can finally turn your security from a game of chance into a reliable, structured defence.
Building Your Cloud Monitoring Framework

A solid cloud security monitoring strategy isn’t something you can just buy off the shelf. It’s a framework you build, piece by piece, with several core pillars working in harmony to give you a complete and resilient defence. Thinking of it this way helps cut through the complexity, turning what feels like an overwhelming task into a clear, manageable structure.
These pillars form a protective shield around your digital assets. For example, real-time threat detection is like a highly sensitive smoke alarm for your infrastructure, sounding the moment it sniffs out trouble. At the same time, compliance monitoring ensures you’re always playing by the rules, much like a building inspector guarantees everything is up to code.
When you understand how these components fit together, you can build a system that doesn’t just react to problems, but actively prevents them. Let’s break down the essential pillars of a modern monitoring framework.
Real-Time Threat Detection and Response
This is the most active, front-line component of your security setup. Real-time threat detection is all about catching malicious activity as it’s happening. It’s not about sifting through logs from last week; it’s about spotting an unauthorised login attempt or suspicious data movement right now.
Think of this as the security guard actively patrolling your digital premises. This system is constantly on the lookout for known attack patterns and any strange behaviours that don’t fit the established baseline of normal activity.
For instance, if a user account that normally only accesses files during business hours in India suddenly starts downloading huge amounts of data from an unrecognised location at 3 AM, the system flags it instantly. This gives your security team a chance to investigate and shut it down before a minor incident blows up into a major breach.
Comprehensive Log Analysis and Management
Your cloud environment is a firehose of data, generating immense volumes of it every single second. Every API call, every user login, every system change they all create a log entry. Buried within this sea of information is the complete story of everything happening across your infrastructure, both good and bad.
Log analysis is the art of collecting, centralising, and making sense of this raw data to turn it into genuinely useful security intelligence. Without it, you just have a record of events with no real understanding of what they mean.
A strong log management strategy is like having a black box flight recorder for your cloud. If an incident occurs, it gives you a precise, unchangeable record of every action taken, which is invaluable for forensic investigation and preventing it from happening again.
Effective log analysis helps you:
- Trace an attacker’s path: Reconstruct the sequence of events during a security breach to figure out exactly what happened.
- Identify insider threats: Spot suspicious activity from legitimate user accounts that could point to misuse of privileges.
- Generate compliance evidence: Provide auditors with the detailed records needed to prove you’re sticking to regulations.
Continuous Compliance Monitoring
Meeting regulations like PCI DSS, HIPAA, or GDPR isn’t a one-and-done project; it’s a constant commitment. The price of non-compliance can be staggering, with some studies putting the average annual cost for an organisation at over $14 million. Continuous compliance monitoring automates the grind of checking your cloud configurations against these regulatory standards.
Instead of performing stressful, manual audits every few months, this kind of system constantly scans your environment. It automatically flags any setting that drifts out of compliance, like an unencrypted database or a poorly configured network access rule. This proactive approach keeps you perpetually audit-ready and dramatically cuts the risk of facing those costly penalties.
Configuration and Posture Management
This final pillar is the very foundation of your security. Configuration management is about creating a complete and accurate inventory of all your digital assets from virtual machines and storage buckets to user identities and access policies. It tells you exactly what you have, where it is, and how it’s configured.
Building on that inventory, Cloud Security Posture Management (CSPM) continuously measures your setup against security best practices. It’s the automated system that checks for those “unlocked doors” we talked about earlier, such as public S3 buckets or overly permissive IAM roles. By giving you a clear, real-time view of your security posture, it helps you find and fix the most critical vulnerabilities first, hardening your defences from the ground up.
Choosing the Right Cloud Security Tools
The world of cloud security tools can feel like a maze, full of confusing acronyms and capabilities that seem to overlap. Picking the right ones is essential for building a solid defence, but first, you have to understand that they don’t all do the same job. Think of it like putting together a specialised team each member has a distinct, vital role in your overall cloud security monitoring strategy.
You wouldn’t ask your building inspector to double as a security guard, right? In the same way, the tool that scans for configuration mistakes is completely different from the one that actively hunts for threats on your network. Getting these differences straight helps you build a layered defence where each tool supports the others, covering all your bases without piling on unnecessary cost or complexity.
Comparing Key Cloud Security Tools
To get a clearer picture, let’s break down the main categories of cloud security tools. Understanding what each one does and where it fits best is the first step toward making an informed decision for your security stack.
| Tool Category | Primary Function | Best For |
|---|---|---|
| Cloud Security Posture Management (CSPM) | Scans cloud environments for misconfigurations, compliance violations, and security risks. | Establishing a strong security baseline and preventing breaches caused by configuration errors. |
| Cloud Workload Protection Platform (CWPP) | Protects individual workloads (servers, containers, serverless functions) from threats at the runtime level. | Securing the applications and services running within your cloud environment. |
| Cloud Detection and Response (CDR) | Monitors real-time activity within the cloud to detect and respond to active threats and attacker behaviour. | Hunting for active attackers who have bypassed preventative controls and are operating inside your network. |
Each of these tools provides a critical piece of the puzzle. A CSPM hardens the foundation, a CWPP protects the assets living on that foundation, and a CDR watches for anyone who manages to sneak past those defences.
Cloud Security Posture Management: The Inspector
The first and most fundamental tool you’ll encounter is Cloud Security Posture Management (CSPM). A CSPM tool is your automated inspector, working 24/7 to scan your entire cloud environment for misconfigurations, compliance gaps, and anything that drifts from security best practices. Its main job is to find weaknesses before an attacker can.
Think of a CSPM as a digital checklist that’s always running. It’s constantly asking critical questions like:
- Are any of our storage buckets accidentally open to the public?
- Do any user accounts have dangerously excessive permissions?
- Are all our databases encrypted correctly?
- Do our network rules line up with compliance standards like PCI DSS?
By giving you a clear, real-time picture of your security posture, a CSPM helps you harden your environment from the ground up. If you want to go deeper, you can explore the fundamentals of cloud security posture management to see how it can form the bedrock of your security programme.
The difference between relying on automation versus manual checks is night and day. It affects everything from how quickly you find issues to how much of your environment you can actually cover.
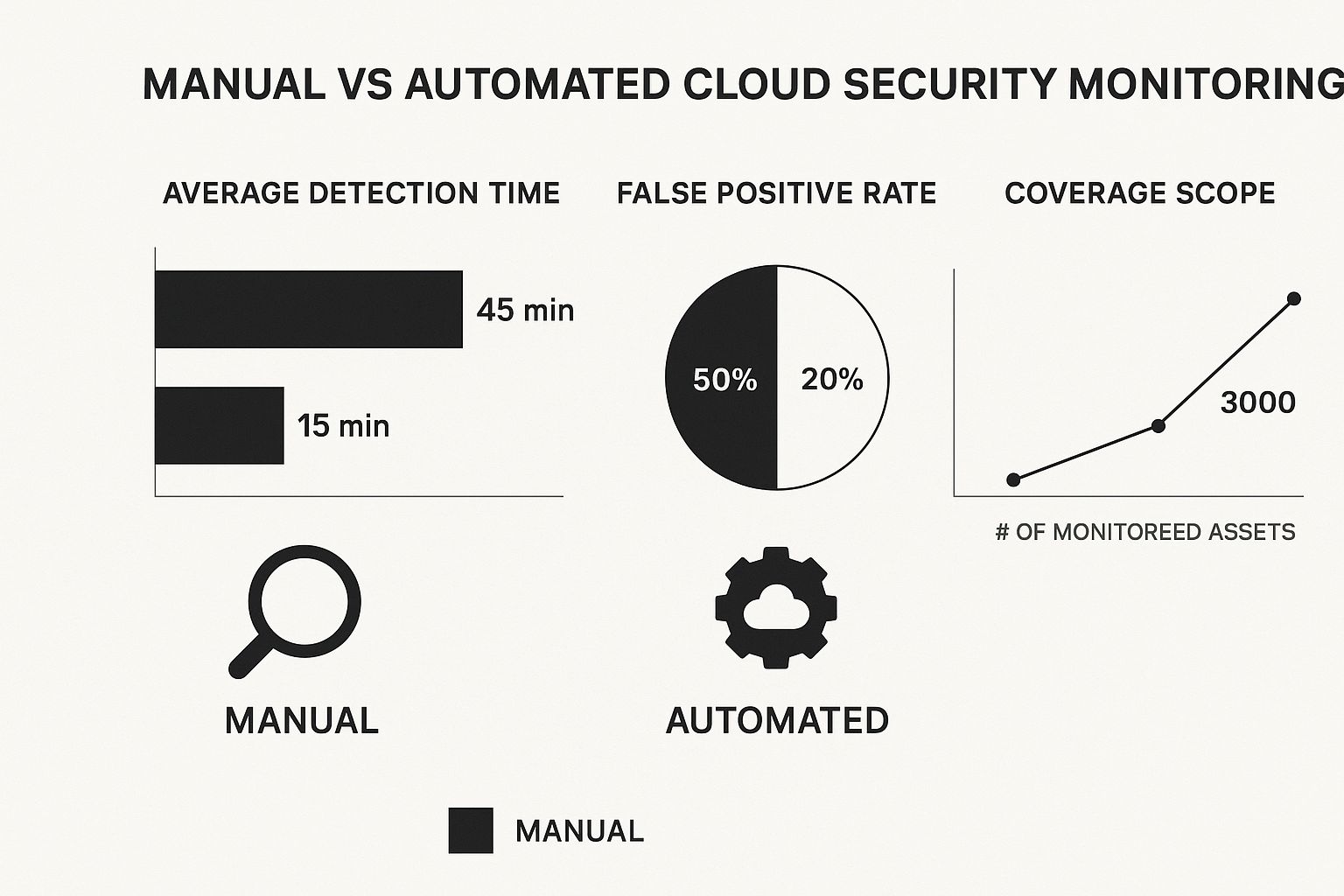
The data speaks for itself. Automation doesn’t just cut detection time from hours to minutes; it also gives you much wider coverage with far fewer false alarms to chase down.
Cloud Workload Protection Platforms: The Bodyguard
While CSPM tools secure the environment, Cloud Workload Protection Platforms (CWPP) secure what’s running inside it. A CWPP is like a dedicated bodyguard for your most important assets: your servers, containers, and serverless functions. It’s laser-focused on protecting these individual workloads from threats, no matter where they happen to be running.
A CWPP does this by giving you visibility and protection right at the source. It can spot malware, block exploits, and enforce security rules directly on the applications and services that run your business. This is absolutely critical because even a perfectly configured environment can be compromised if there’s a vulnerability hiding in the application code itself.
Cloud Detection and Response: The Threat Hunter
The most advanced layer of cloud security monitoring comes from Cloud Detection and Response (CDR) tools. If a CSPM is the inspector and a CWPP is the bodyguard, then CDR is your elite threat hunter. It actively sifts through runtime activity to catch attackers who have slipped past your other defences. This is becoming more important every single day.
Security teams are drowning in alerts. For instance, in the Asia-Pacific region, which includes India, there’s been a staggering 388% increase in cloud-based alerts in 2024 as attackers ramp up their efforts. This flood of notifications makes it nearly impossible for teams to tell what’s a real threat and what’s just noise.
CDR tools cut through this chaos by focusing on real-time activity. They monitor compute instances, container hosts, and serverless functions to identify malicious runtime behaviours, providing the critical context needed to respond effectively.
These tools are essential for catching active threats in the act like an attacker trying to move sideways across your network or steal your data. By combining these different tools, you create a powerful, multi-layered security system that can both prevent attacks and respond to them when they happen.
Putting Your Monitoring Plan Into Action
Having a solid strategy is one thing; turning it into a real, functioning security shield for your cloud environment is another entirely. This is where the rubber meets the road, moving from high-level planning to hands-on execution. We’re about to transform that theoretical framework into an active, practical defence.
The entire process kicks off with a simple but vital question: what are we actually protecting? Before you even think about deploying a tool, you must have a crystal-clear understanding of your security goals and your most valuable assets. These are your ‘crown jewels’ the data, applications, and infrastructure that your business simply cannot function without.
Trying to protect everything equally is a recipe for failure. By first pinpointing your most critical assets, you can concentrate your resources where they’ll make the biggest difference. This foundational step ensures your most important data gets the highest level of protection and will guide every single decision you make from here on out.
Define Your Security Goals and Identify Key Assets
First things first, you need to define what success actually looks like. Your security goals can’t be vague; they must be specific, measurable, and tied directly to what the business cares about. Are you laser-focused on achieving compliance with a regulation like PCI DSS, or is your absolute top priority preventing sensitive data from being exfiltrated?
Once your goals are set, it’s time to take inventory of your ‘crown jewel’ assets. This might include:
- Sensitive Customer Data: Think databases packed with personally identifiable information (PII) or financial details.
- Proprietary Code: The source code and intellectual property that give your company its competitive edge.
- Critical Applications: Your customer-facing services that actually bring in revenue.
- Infrastructure Control Planes: The core administrative dashboards for your entire cloud environment.
Knowing your priorities allows you to tailor your monitoring efforts with precision. For instance, the monitoring rules you apply to a database holding sensitive customer data will be infinitely stricter than those for a public-facing marketing website. Understanding the specific cloud security risks tied to these assets will help you build a much smarter strategy.
Select and Deploy the Right Tools
With your goals and assets clearly defined, you can now start choosing the right tools for the job. The tools you pick will depend heavily on your cloud provider whether you’re on AWS, Azure, or Google Cloud—and the specific security gaps you need to plug.
A great starting point is to switch on the native security services your cloud platform already offers, like AWS CloudTrail, Azure Monitor, or Google Cloud’s operations suite. These native tools give you a baseline of visibility and are built to work perfectly within their own ecosystems.
However, these tools often need backup. To get a truly comprehensive security posture, you’ll likely need to augment them with third-party solutions. Think about deploying a mix of CSPM, CWPP, and CDR tools to create a layered defence that covers misconfigurations, workload vulnerabilities, and active threats.
The goal isn’t just to collect mountains of data; it’s to get actionable insights. A well-integrated toolset should connect the dots between different sources, helping your team separate the real threats from all the background noise and focus on what truly matters.
This integration is the key to avoiding alert fatigue. When your security team is drowning in notifications, they’ll inevitably start missing the critical ones.
Establish Clear Incident Response Procedures
Getting an alert is just the beginning of the story. Without a clear, documented plan for what to do next, even the most advanced cloud security monitoring system falls short. An incident response plan is your playbook for a crisis, outlining every step from the moment an issue is detected to its final resolution.
Your plan needs to answer some crucial questions:
- Who is responsible? Define clear roles for who investigates, who contains the threat, and who handles communication.
- What is the escalation path? Detail who gets notified and when, from the on-the-ground technical teams all the way up to executive leadership.
- How do we contain the threat? Specify the exact technical steps needed to isolate a compromised machine or account and stop the bleeding.
- How do we recover? Outline the process for restoring systems and data from clean, secure backups.
Don’t just write this plan and let it gather dust. Test it regularly with drills and tabletop exercises. A plan that only exists on paper is almost guaranteed to fail under the pressure of a real incident. Practice is what ensures your team can act quickly, confidently, and effectively when it counts the most.
Frequently Asked Questions
Even with the best plan in place, stepping into cloud security monitoring can feel a bit like navigating a new city. It’s perfectly normal to have questions. The cloud just doesn’t operate like the traditional IT environments we’re used to, and getting a handle on those differences is the key to building a solid defence.
This section tackles some of the most common hurdles and questions we see organisations run into. We’ll give you straightforward, practical answers to help clear up the confusion and get you moving forward with confidence.
Isn’t Cloud Security My Provider’s Responsibility?
This is probably the single most common and most dangerous misconception out there. It all comes down to a misunderstanding of the Shared Responsibility Model. While it’s true that your cloud provider (like AWS, Azure, or Google Cloud) handles securing the underlying infrastructure, that’s only half the story.
They take care of the security of the cloud. Think of them as securing the physical building, the power grid, and the hardware that everything runs on. But you are 100% responsible for the security of what you put in the cloud.
Your side of the deal includes:
- Managing User Access: You decide who gets the keys to which doors. This means setting up permissions and making sure no one has more access than they absolutely need (the principle of least privilege).
- Configuring Security Settings Correctly: It’s on you to ensure your storage buckets aren’t left open to the public, your firewalls (security groups) are configured correctly, and your data encryption is switched on.
- Protecting Your Data: The data itself classifying it, encrypting it, and protecting it from theft or leakage is entirely your responsibility.
- Actively Monitoring for Threats: You need to be the one watching your own house for suspicious activity, configuration mistakes, and compliance slip-ups.
Cloud security monitoring tools are what you use to hold up your end of this critical bargain. They give you the eyes and ears you need to see what’s happening and ensure your configurations, apps, and data are actually safe.
How Is Cloud Monitoring Different From On-Premise Monitoring?
While the goal is the same find and stop threats the way you get there couldn’t be more different. For years, on-premise security was all about building a fortress. You had a clearly defined network perimeter, a digital moat you had to defend.
Cloud environments blow that entire concept apart. They are dynamic, constantly changing, and have no real perimeter to speak of. Resources can be created, reconfigured, and deleted in minutes. The old “castle and moat” strategy is simply obsolete, which means you need a whole new security playbook.
Cloud security monitoring is API-driven, automated, and designed for constant change. It’s built for an environment where the attack surface is fluid and identity, not location, is the new perimeter.
This fundamental shift means cloud security monitoring focuses heavily on areas that were often secondary in the old world:
- Identity and Access Management (IAM): In the cloud, who is doing something is often far more important than where they’re doing it from. Keeping a close eye on IAM policies and roles is absolutely critical.
- Configuration Drift: A secure setting today might be insecure tomorrow. A core job of cloud monitoring is to constantly check for changes that deviate from your secure baseline, as simple misconfigurations are a primary entry point for attackers.
- API Activity Logs: Attackers use APIs to navigate and exploit cloud environments. Monitoring these logs for unusual calls or patterns is your front line for detecting threats as they happen.
Can We Manage Cloud Monitoring Without a Dedicated Team?
For smaller organisations, this is a very real challenge. While modern tools have incredible automation that does a lot of the heavy lifting, effective monitoring still needs a human touch. Someone has to set up the rules, investigate the alerts that pop up, and coordinate a smart response.
This is exactly why many businesses, particularly those without a big in-house security team, decide to work with a Managed Security Service Provider (MSSP). A good cloud MSSP can offer 24/7 expert monitoring and response, giving you top-tier protection without the massive overhead of hiring and training your own team.
For larger companies with more resources, building an in-house Cloud Security Operations Centre (SOC) is often the right move. A dedicated team brings deep knowledge of the business, can work closely with developers, and gives you ultimate control over your security programme. The right choice really comes down to your organisation’s size, budget, and how much risk you’re willing to accept.
What Is the Best First Step to Improve Our Cloud Monitoring?
If you’re staring at the mountain and wondering where to start climbing, the most impactful first step is almost always the same: get visibility and start fixing misconfigurations. These are the unlocked doors and open windows of your cloud environment the low-hanging fruit for attackers.
Your best move is to implement a Cloud Security Posture Management (CSPM) tool. Think of a CSPM as an automated security auditor that gives you immediate wins:
- Comprehensive Scanning: It will automatically sweep your entire cloud footprint, checking it against hundreds of security best practices and compliance rules.
- Prioritised Findings: It won’t just dump a list of problems on you. It will highlight the biggest risks first, like public storage buckets, overly generous access rights, or unencrypted data.
- Actionable Remediation: Crucially, it will give you clear, step-by-step instructions on how to fix the issues it finds, so your team can start making improvements right away.
By starting with a CSPM, you immediately shrink your attack surface and build a solid, secure foundation. It’s about locking the doors and windows first. Once that’s done, you can move on to setting up the more advanced alarm systems for active threat detection.
Ready to build a secure, resilient, and high-performing cloud foundation? The expert team at Signiance Technologies can guide you. We specialise in designing and managing cloud architectures that are not only powerful but also secure from the ground up. Discover how our cloud solutions can protect and accelerate your business.
