In the world of Linux, think of file permissions as the keys to your house. These permissions determine who can enter (access), rearrange the furniture (modify), or even throw a party (execute programs) in your digital home. Understanding and managing these permissions is like being a wise homeowner who knows exactly who has keys to their house and which doors they open.
The Basics of Linux Permissions
Linux permissions are like the guest list for your house, specifying what your guests (users, groups, and others) can and cannot do. Here’s a quick breakdown:
- User: The person who created the file. They’re like the homeowner.
- Group: A group of users who share certain permissions. Think of them as your family members who live in the house.
- Others: Everyone else who isn’t the owner or in the group. Imagine them as the neighbors.

Permissions are given out using a simple numeric system where:
- Read (r) is like letting someone view the pictures on your walls = 4
- Write (w) is like allowing them to rearrange the furniture = 2
- Execute (x) is like permitting them to open your home’s door = 1
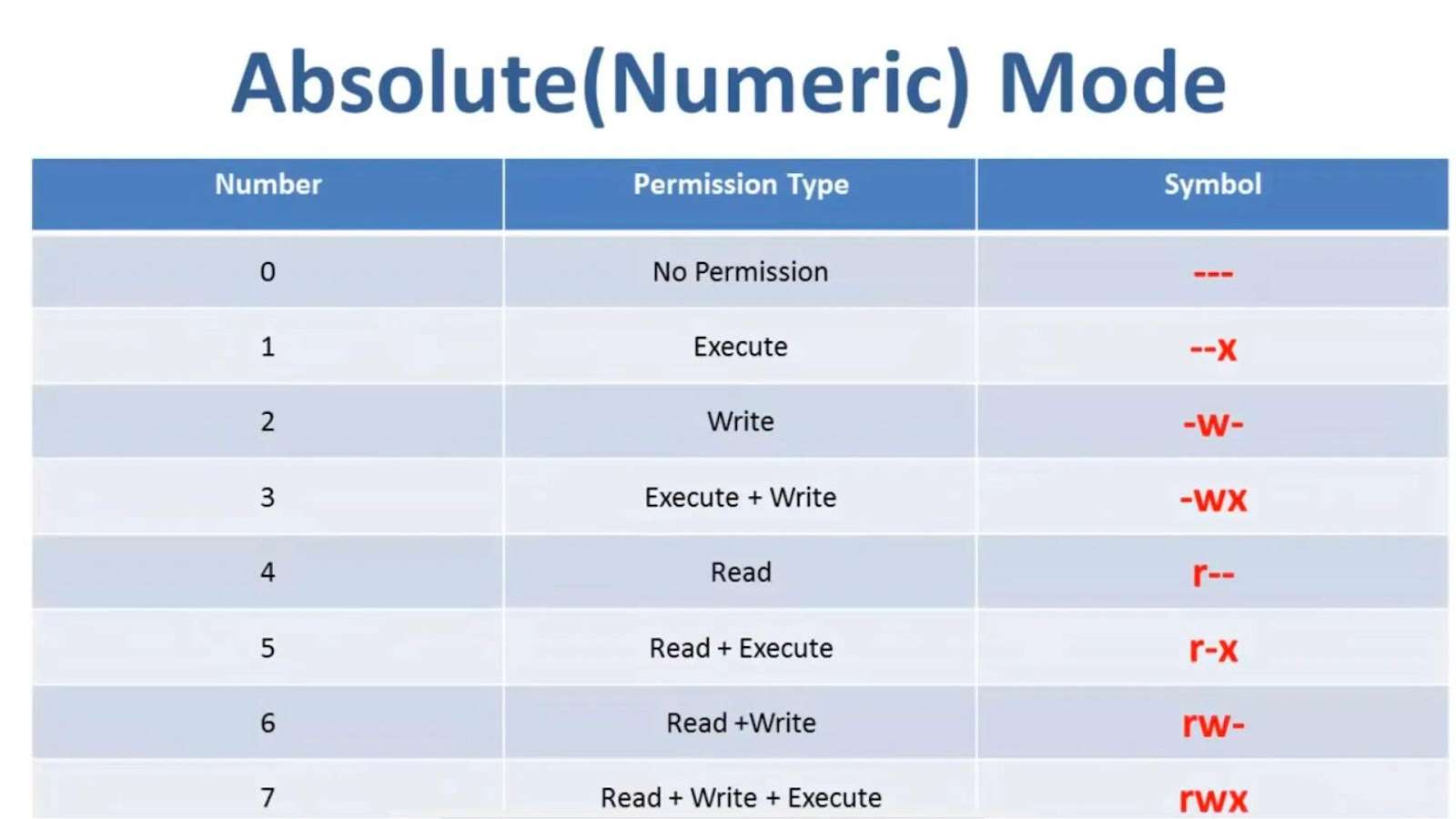
By adding these numbers, you set the house rules for accessing your files. For instance, chmod 400 filename means only you can look at the file, no touching or using it otherwise.
Smart Security Practices
- Minimalist Key Strategy: Only hand out keys (permissions) that are absolutely necessary. Regularly check and adjust who has access to what, and don’t forget to collect the keys once their job is done.
- Avoid the Master Key: Using the root account for daily tasks is risky. Encourage the use of individual accounts with specific permissions.
- Role-Based Key Allocation: In a shared space, distribute keys based on what each person needs to do. This method keeps your digital house orderly and secure.
Protecting Your Digital Valuables
- Secure the Crown Jewels: Important files need extra protection. Tools like SELinux or AppArmor act as high-tech security systems.
- Default Security Settings (umask): When creating new files or folders, umask ensures they’re born with a basic level of security, preventing them from being too open.
Umask: The Secret to Default Security
Imagine every new file or folder comes with a potential set of keys. Umask is your guideline on which keys not to hand out by default, ensuring new items start with a safe level of access.
Wrapping Up
Understanding Linux permissions is like learning the best practices for home security. It’s about being mindful of who has access to what, ensuring your digital space remains secure, orderly, and welcoming to the right people. By adopting smart permission practices and utilizing tools like umask, you can protect your system while making it a productive environment for its users.
With these guidelines, you’re not just a homeowner; you’re a wise guardian of your digital domain. Welcome to the world of Linux security—where the power to protect is in your hands.
