Protecting Your Cloud Assets in 2025
Cloud security is crucial for protecting your business. This listicle presents eight cloud security best practices for startups, enterprises, and IT professionals in the IN region. Learn how to implement essential security measures, from Identity and Access Management (IAM) to incident response, and safeguard your cloud assets. These strategies cover data encryption, network security, continuous monitoring, automated testing, cloud configuration, data loss prevention, and disaster recovery. Mastering these cloud security best practices is critical for minimizing risks and ensuring business continuity.
1. Identity and Access Management (IAM)
Identity and Access Management (IAM) is a crucial component of cloud security best practices, forming the bedrock of controlling access to your valuable cloud resources. It’s a framework of policies and technologies that ensures only authorized users have the appropriate level of access to specific technology resources. In the cloud, IAM gives you granular control over who can perform what action on which resource, implementing the principle of least privilege – a cornerstone of robust security. This means users only get access to the specific resources they need to do their job, and nothing more. This minimizes the potential damage from compromised credentials or insider threats.

IAM systems typically encompass several key features, including Role-based access control (RBAC), Multi-factor authentication (MFA), Single sign-on (SSO) capabilities, Privileged access management, and User lifecycle management. RBAC allows you to group users with similar responsibilities and assign permissions to those roles, simplifying administration. MFA adds an extra layer of security by requiring multiple forms of authentication, making it significantly harder for attackers to gain access even if they obtain a password. SSO streamlines user access by allowing them to use one set of credentials to access multiple applications, while privileged access management provides enhanced security for highly sensitive accounts. Finally, user lifecycle management automates user onboarding and offboarding, ensuring access is revoked when an employee leaves the company.
Why IAM Deserves Its Place as a Top Cloud Security Best Practice:
In today’s distributed and complex cloud environments, safeguarding data and resources against unauthorized access is paramount. IAM provides the foundation for a secure cloud posture. It reduces the risk of data breaches, simplifies compliance audits by providing detailed access logs, and centralizes user management, making it easier to manage access across your entire cloud infrastructure. This is especially critical for startups and early-stage companies looking to scale securely, enterprise IT departments managing complex environments, and cloud architects and developers building secure applications.
Examples of Successful Implementation:
- AWS IAM: Allows for fine-grained permissions control and supports MFA for all admin accounts, offering a robust solution for securing AWS resources.
- Azure Active Directory: Microsoft’s enterprise-wide SSO solution integrates seamlessly with Azure services, providing a centralized identity management platform.
- Google Cloud IAM: Enables service accounts and workload identity federation, offering flexible access management for various application scenarios. Okta and Ping Identity provide cross-platform IAM solutions extending SSO and other IAM features to a wide range of applications and cloud providers.
Pros:
- Reduced risk of unauthorized access and data breaches
- Provides comprehensive audit trails for compliance requirements
- Centralizes user management, simplifying administration
- Enables fine-grained permissions for precise access control
Cons:
- Can be complex to implement correctly, requiring careful planning and execution
- Requires regular review and maintenance to stay aligned with evolving security needs
- May create bottlenecks if permissions are too restrictive, impacting productivity
Actionable Tips for Implementing IAM Effectively:
- Least Privilege: Implement the principle of least privilege by default. Grant only the necessary permissions for each user or role.
- MFA Everywhere: Enable MFA for all user accounts, especially for administrative access. This drastically reduces the risk of unauthorized access.
- Regular Audits and Rotations: Regularly audit access logs and rotate access keys and credentials to minimize the impact of compromised credentials.
- Managed Identities: Use managed identities or service accounts for applications instead of hardcoded credentials. This improves security and simplifies credential management.
- Just-in-Time Access: Implement just-in-time access for privileged operations, granting elevated permissions only when needed and revoking them immediately afterward.
By prioritizing IAM and following these best practices, organizations in the IN region and beyond can significantly enhance their cloud security posture and protect their valuable data and resources in the ever-evolving threat landscape.
2. Data Encryption: A Cornerstone of Cloud Security Best Practices
Data encryption is a fundamental aspect of cloud security best practices, transforming readable data into an unreadable format (ciphertext) to prevent unauthorized access. This process safeguards sensitive information in the cloud across three key states: data at rest (stored data), data in transit (data moving between locations, such as across networks), and increasingly, data in use (data being actively processed). Encryption acts as a critical security control, ensuring data protection even if other security layers are compromised. It’s essential for any organization storing or processing sensitive data in the cloud, contributing significantly to robust cloud security posture.

Several encryption methods cater to different cloud security needs:
- Encryption at rest: Secures data stored in databases, object storage, and file systems. Cloud providers often offer default encryption at rest, but understanding these defaults and configuring them appropriately is crucial.
- Encryption in transit: Protects data as it travels across networks, typically using TLS/SSL protocols. This safeguards against man-in-the-middle attacks and ensures secure communication between clients and servers.
- Client-side encryption: Data is encrypted before being sent to the cloud, giving the user complete control over the encryption keys.
- Envelope encryption with key management: Combines symmetric and asymmetric encryption. Data is encrypted with a fast symmetric key, which is then encrypted with a public key associated with the recipient.
- Homomorphic encryption and confidential computing: Emerging technologies enabling computations on encrypted data without decryption, opening new possibilities for secure data processing in the cloud.
Why Data Encryption Deserves Its Place in the List:
Data breaches are a constant threat, and encryption is a primary defense against data exposure. By rendering data unintelligible to unauthorized parties, encryption minimizes the impact of a breach. Furthermore, complying with data privacy regulations like GDPR and HIPAA often mandates data encryption. For businesses in IN, adhering to these regulations is critical for avoiding penalties and maintaining customer trust.
Pros:
- Strong data protection: Shields sensitive data from unauthorized access, even if other security controls fail.
- Compliance: Helps meet regulatory requirements for data protection.
- Breach mitigation: Reduces the impact of data breaches by rendering stolen data unusable.
- Enhanced security posture: Demonstrates a commitment to security, building trust with customers and partners.
Cons:
- Performance impact: Can introduce latency if not implemented efficiently.
- Key management complexity: Securely storing and managing encryption keys is essential. Lost keys can mean permanent data loss.
- Potential data loss: Mismanagement of encryption keys can result in irreversible data loss.
- Limited functionality: Certain features like search and indexing might be impacted by encryption.
Examples of Successful Implementation:
- AWS Key Management Service (KMS) and S3 bucket encryption enable robust data protection within the AWS ecosystem.
- Google Cloud Platform offers default encryption at rest for many of its services, providing a baseline level of security.
- Microsoft Azure’s Storage Service Encryption allows for server-side encryption of data stored in Azure Storage.
- Financial institutions leverage field-level encryption within cloud databases to protect sensitive Personally Identifiable Information (PII).
Actionable Tips for Implementing Data Encryption:
- Use strong algorithms: Employ industry-standard encryption algorithms like AES-256 and RSA-2048.
- Robust key management: Implement a secure key management system with regular key rotation. Consider BYOK (Bring Your Own Key) for increased control over encryption keys, especially for sensitive data.
- Encrypt everything: Encrypt all sensitive data, both at rest and in transit. Don’t overlook data in transit between services within your cloud environment.
- TLS 1.2+: Enforce TLS 1.2 or higher for all API connections and data transfers.
- Performance testing: Thoroughly test the performance impact of encryption to minimize latency and ensure optimal application performance.
By implementing robust data encryption practices, organizations in IN can significantly improve their cloud security posture, protect sensitive data, and comply with relevant regulations. From startups to enterprise IT departments, understanding and implementing data encryption is crucial in today’s cloud-centric world.
3. Network Security and Segmentation
Network security and segmentation is a crucial cloud security best practice that involves controlling access to and within your cloud environment. It’s about building robust barriers and checkpoints within your cloud infrastructure to prevent unauthorized access, contain security breaches, and protect sensitive data. This practice leverages the power of virtualization to create isolated network segments, allowing you to apply granular security policies and restrict traffic flow based on the principle of least privilege. This means granting only the necessary access permissions required for a given task or resource, thereby minimizing the potential impact of security incidents.

This method works by dividing your cloud environment into smaller, isolated networks called Virtual Private Clouds (VPCs) and further subdividing them into subnets. Security groups act as virtual firewalls for your cloud resources, controlling inbound and outbound traffic at the instance level. Network Access Control Lists (NACLs) provide an additional layer of security, filtering traffic at the subnet level. Think of it like having multiple layers of security guards at different checkpoints, each with specific instructions on who to allow through.
Features driving Network Security and Segmentation:
- Virtual Private Clouds (VPCs) and Subnets: Foundation for isolating your cloud environment.
- Security Groups and Network ACLs: Granular control over traffic flow based on rules and policies.
- Web Application Firewalls (WAFs): Protect web applications from common web exploits and attacks.
- DDoS Protection: Mitigates distributed denial-of-service attacks that can overwhelm your resources.
- Private Connectivity Options (VPN, Direct Connect): Establish secure connections between your on-premises infrastructure and your cloud environment.
- Micro-segmentation: Isolates individual workloads within a data center or cloud environment.
Benefits of Implementing Network Security and Segmentation:
- Limits the Blast Radius: Contains security breaches within a specific segment, preventing them from spreading to the entire environment. This is especially critical for businesses in IN, where the digital landscape is rapidly evolving and cyber threats are becoming increasingly sophisticated.
- Defense-in-Depth: Multiple layers of security create a robust defense against a wide range of threats.
- Granular Traffic Control: Fine-grained control over network traffic allows you to enforce strict security policies and meet compliance requirements.
- Secure Hybrid Cloud Architectures: Enables secure integration of on-premises and cloud environments.
Pros and Cons:
- Pros: Limits the blast radius of security breaches, provides defense-in-depth, allows granular traffic control, enables secure hybrid cloud architectures.
- Cons: Can introduce complexity in network design, may require specialized expertise, potential performance impact from additional security layers, can be challenging to retrofit to existing deployments.
Examples of Successful Implementation:
- Financial services in India implementing strict network segmentation for PCI-DSS compliance.
- Healthcare organizations using private links for secure patient data transfer, adhering to data privacy regulations.
- Global companies like Netflix implementing micro-segmentation for their microservices architecture.
Actionable Tips for Readers:
- Design with Security in Mind: Integrate network security considerations from the initial stages of your cloud architecture design.
- Utilize Private Subnets: Deploy backend services and databases within private subnets, shielding them from direct internet access.
- Implement WAFs: Protect all public-facing applications with Web Application Firewalls.
- Leverage Private Connectivity: Use VPC endpoints or private links to securely access cloud services without exposing them to the internet.
- Inspect East-West Traffic: Implement security measures not just for north-south traffic (internet to cloud) but also for east-west traffic (within the cloud).
- Regularly Review and Audit: Continuously monitor and audit your security group rules to ensure they remain relevant and effective.
Why This Deserves Its Place in the List:
Network security and segmentation is fundamental to any cloud security best practices list. It provides a strong foundation for protecting your cloud resources, mitigating threats, and achieving compliance. For organizations in IN navigating the complexities of the cloud, robust network security is non-negotiable. This approach directly addresses the growing concern of data breaches and provides a proactive approach to safeguarding valuable data. It empowers businesses, from startups to enterprises, to confidently embrace the cloud while maintaining a strong security posture. Though there can be added complexity, the benefits in terms of enhanced security far outweigh the potential challenges. By segmenting their networks, organizations can effectively minimize the attack surface and ensure the integrity and confidentiality of their data in the cloud.
4. Continuous Security Monitoring and Threat Detection
In today’s dynamic cloud environments, implementing robust cloud security best practices is paramount, and continuous security monitoring and threat detection is a cornerstone of this approach. This proactive practice involves continuously collecting, analyzing, and correlating security data from your cloud infrastructure to identify threats, anomalies, and potential security incidents in real-time. This provides essential visibility into your cloud security posture, enabling rapid response and minimizing the impact of security events.
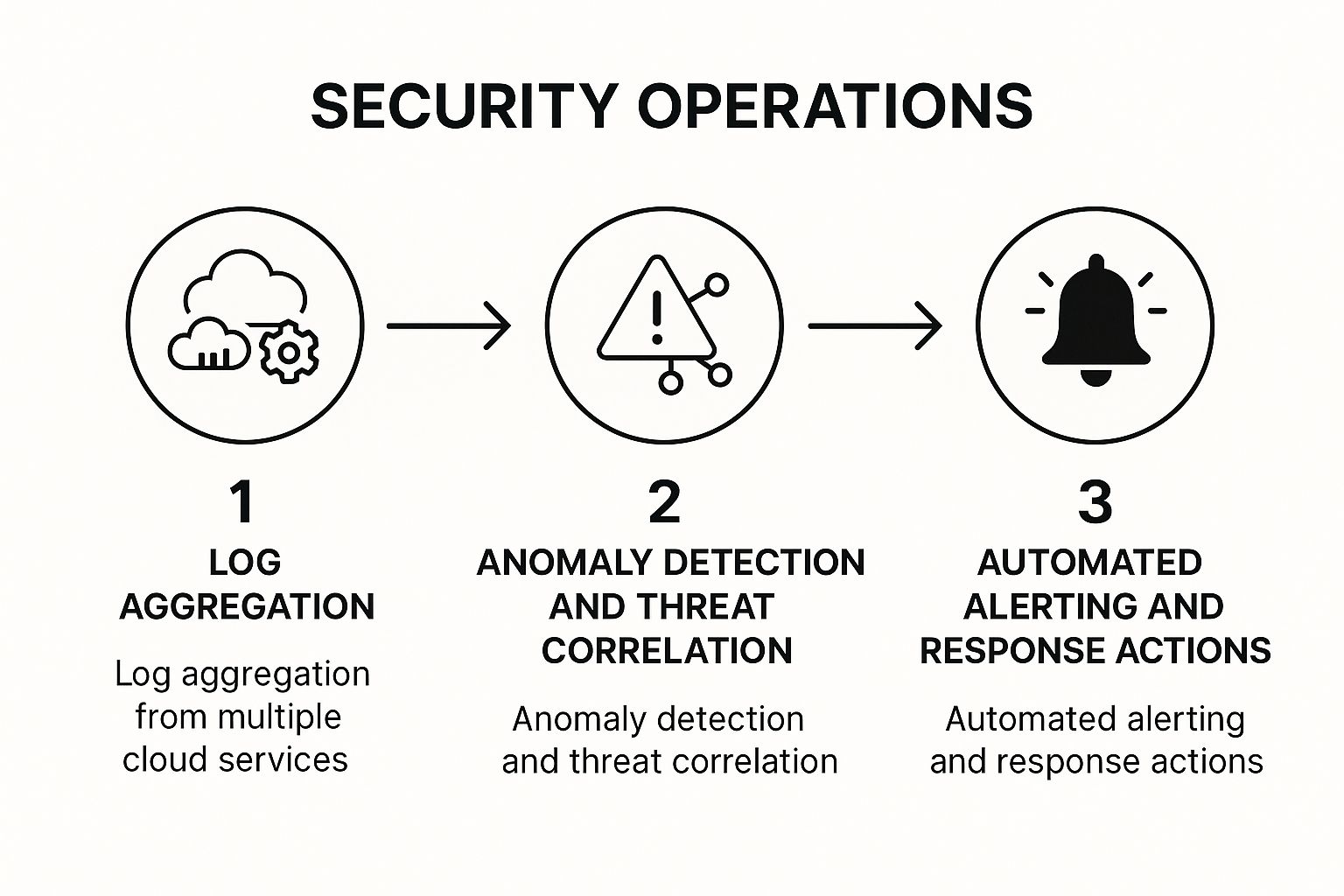
The infographic above visualizes the continuous security monitoring process flow. It begins with data collection from various sources like logs, events, and threat intelligence feeds. This data is then processed and analyzed for anomalies and threats. Finally, the system triggers alerts and automated responses based on predefined rules and policies. The interconnected nature of these steps highlights the importance of a holistic approach to cloud security. Early detection, as visualized, is crucial for swift incident response and mitigation.
This process flow underscores the importance of proactive monitoring and rapid response. From data aggregation to automated remediation, each step plays a critical role in maintaining a secure cloud environment.
Features like log aggregation and analysis, Security Information and Event Management (SIEM) integration, behavioral analytics, threat intelligence integration, automated alerting, vulnerability scanning, and incident response mechanisms form the core of effective continuous security monitoring. These features provide the tools necessary to detect and respond to a wide range of security threats.
When and Why to Use Continuous Security Monitoring:
Continuous monitoring is essential for organizations of all sizes operating in the cloud, especially for startups and enterprises in the IN region experiencing rapid digital transformation. It’s particularly beneficial when:
- Dealing with complex cloud environments: Maintaining visibility across distributed systems can be challenging. Continuous monitoring provides a centralized view of security across your entire cloud footprint.
- Facing evolving threats: The threat landscape is constantly changing. Continuous monitoring helps you stay ahead of emerging threats and vulnerabilities.
- Needing to meet compliance requirements: Many industry regulations, like GDPR and HIPAA, mandate continuous security monitoring.
- Prioritizing rapid incident response: Early detection minimizes the impact of security breaches. Continuous monitoring enables swift response and remediation.
Examples of Successful Implementation:
Several organizations have demonstrated the effectiveness of continuous security monitoring. Capital One uses AWS CloudTrail and GuardDuty for threat detection. Netflix employs security monitoring with real-time alerting and automated remediation, and Airbnb leverages centralized logging and anomaly detection. These examples showcase how continuous monitoring can be tailored to various organizational needs.
Pros and Cons:
While offering significant advantages, continuous security monitoring also has its challenges:
Pros:
- Reduced detection and response time
- Increased visibility across cloud environments
- Detection of sophisticated attacks
- Data for compliance and forensics
Cons:
- Potential for alert fatigue
- Requires skilled security analysts
- Potential high costs
- Complexity in correlating events
Actionable Tips:
- Enable comprehensive logging across all cloud services.
- Implement automated responses for common security events.
- Leverage machine learning for anomaly detection to reduce false positives.
- Consider establishing a Security Operations Center (SOC) or Managed Detection and Response (MDR) service.
- Develop clear incident response playbooks.
- Regularly test your detection capabilities through purple team exercises.
Popular Tools and Services:
Several tools and services facilitate continuous security monitoring. These include AWS CloudTrail, GuardDuty, and Security Hub; Azure Security Center and Sentinel; Google Cloud Security Command Center; Splunk Cloud; and Datadog Security Monitoring.
This video further elaborates on the principles of continuous security monitoring and provides practical insights for implementation.
By embracing continuous security monitoring as a core cloud security best practice, organizations in the IN region can effectively safeguard their data, applications, and infrastructure in the face of ever-evolving threats. This proactive approach ensures business continuity, protects sensitive information, and fosters trust with customers and stakeholders.
5. Automated Security Testing and Vulnerability Management
In the realm of cloud security best practices, automated security testing and vulnerability management stand as a crucial pillar for safeguarding your valuable data and infrastructure. This proactive approach integrates security checks throughout the entire development lifecycle, enabling you to identify and address vulnerabilities early, significantly reducing the potential for costly breaches and disruptions. This is especially vital in today’s fast-paced development environments and is a core component of a robust DevSecOps strategy.
How it Works:
Automated security testing involves employing a suite of tools and techniques to automatically scan your code, infrastructure, and applications for security flaws. This encompasses various testing methodologies including:
- Static Application Security Testing (SAST): Analyzes your source code without actually executing it, identifying potential vulnerabilities like SQL injection and cross-site scripting.
- Dynamic Application Security Testing (DAST): Tests the running application, simulating real-world attacks to uncover vulnerabilities like authentication bypasses and insecure API endpoints.
- Infrastructure as Code (IaC) Security Scanning: Evaluates your IaC templates (e.g., Terraform, CloudFormation) for security misconfigurations before they are deployed, preventing vulnerabilities in your cloud infrastructure.
- Container Image Scanning: Analyzes container images for known vulnerabilities in the underlying operating system, libraries, and application dependencies.
- Software Composition Analysis (SCA): Identifies open-source components used in your application and checks for known vulnerabilities or license compliance issues.
These testing methods, coupled with continuous vulnerability management, create a closed-loop system. Vulnerabilities are identified, prioritized based on risk, and then remediated systematically, ensuring a continuous cycle of improvement.
Why This is a Cloud Security Best Practice:
This proactive approach drastically reduces the cost and impact of security breaches. Detecting and fixing vulnerabilities during development is significantly cheaper than addressing them in production, where the consequences can include data loss, reputational damage, and regulatory fines. For startups and enterprises in the IN region, adhering to global security standards is increasingly important for attracting investment and maintaining customer trust. This practice demonstrates a commitment to security and helps build confidence in your platform.
Examples of Successful Implementation:
Industry leaders have demonstrated the effectiveness of automated security testing:
- Google: Employs continuous security scanning for all code commits, catching vulnerabilities before they reach production.
- Microsoft: Integrates automated security gates into their DevSecOps practices, preventing vulnerable code from being deployed.
- Intuit: Uses a shift-left security approach with integrated scanning tools, ensuring security is considered from the very beginning of the development process.
Actionable Tips:
- Integrate security scanning into your CI/CD pipelines: This automates the testing process and ensures that every code change is checked for vulnerabilities.
- Establish security gates: Prevent the deployment of code containing critical vulnerabilities.
- Use a risk-based approach to prioritize vulnerability remediation: Focus on fixing the most critical vulnerabilities first.
- Implement automated patching where possible: Streamline the patching process and reduce the window of vulnerability.
- Combine multiple testing approaches (SAST, DAST, SCA, etc.) for comprehensive coverage: Different tools uncover different types of vulnerabilities.
- Establish SLAs for vulnerability remediation based on severity: Ensure timely resolution of security issues.
Pros:
- Early detection of security issues
- Reduced cost of remediation
- Consistent application of security standards
- Scalable across large cloud environments
Cons:
- Can produce false positives requiring triage
- Tool integration complexity in CI/CD pipelines
- Keeping up with new vulnerability types
- Potential delays in development if not properly implemented
Popularized By: Snyk, Aqua Security, Prisma Cloud (Palo Alto Networks), GitLab Security, SonarQube, Tenable. These vendors offer a range of tools and services to help implement automated security testing and vulnerability management.
By adopting automated security testing and vulnerability management, organizations in the IN region can build more secure and resilient cloud environments, mitigating risk and establishing a strong security posture in the face of ever-evolving threats. This best practice is not merely a technical necessity but a strategic imperative for success in the cloud-driven world.
6. Cloud Configuration and Compliance Management
Cloud configuration and compliance management is a critical aspect of cloud security best practices, especially crucial for startups, enterprises, and DevOps teams in the IN region and globally. It encompasses the processes of establishing, monitoring, and enforcing secure configurations for your cloud resources, ensuring your cloud environment adheres to organizational policies, industry standards like CIS Benchmarks, and regulatory requirements. This proactive approach helps prevent security breaches arising from misconfigurations, a surprisingly common vulnerability in cloud environments.
This method works by defining a desired state for your cloud resources and continuously monitoring them against that state. This involves implementing security best practices and leveraging automated tools to detect and remediate any deviations, known as configuration drift. By automating these processes, organizations can ensure consistent security across their cloud footprint, even as it scales.
Why is this a crucial cloud security best practice? Because misconfigurations are a leading cause of cloud breaches. A simple error in access control, for example, can expose sensitive data to unauthorized users. Configuration and compliance management minimizes this risk.
Features and Benefits:
Several key features contribute to effective cloud configuration and compliance management:
- Cloud Security Posture Management (CSPM): These tools provide continuous visibility into your cloud environment’s security posture, identifying misconfigurations and compliance violations.
- Infrastructure as Code (IaC) Policy Enforcement: Integrating security policies directly into your IaC templates ensures that resources are deployed securely from the start.
- Automated Remediation of Misconfigurations: Automatically fixing identified issues reduces manual effort and speeds up response times.
- Compliance Monitoring and Reporting: Generate reports to track compliance with various standards and regulations, simplifying audits.
- Continuous Configuration Validation: Ongoing validation ensures that configurations remain secure and compliant over time.
- Resource Tagging and Inventory Management: Tagging resources allows for efficient organization, security classification, and ownership tracking.
Pros:
- Prevents common cloud misconfigurations that lead to breaches.
- Provides continuous compliance assurance.
- Reduces manual effort through automation.
- Enables rapid scaling while maintaining security standards.
Cons:
- Keeping policies updated with the constantly evolving cloud services landscape can be challenging.
- Balancing security with operational flexibility requires careful planning.
- Managing exceptions for legitimate business cases needs a clear process.
- Potential false positives in complex environments require investigation.
Examples of Successful Implementation:
- Capital One: Implemented automated guardrails for their AWS environments, ensuring consistent security policies across their cloud footprint.
- Airbnb: Uses automated configuration validation and remediation to quickly address misconfigurations and maintain a secure environment.
- Dow Jones: Implemented compliance automation for their multi-cloud environment, simplifying compliance management across different cloud providers.
Actionable Tips for Implementation:
- Implement Infrastructure as Code (IaC) with built-in security policies: Tools like Terraform with Sentinel or CloudFormation Guard can help.
- Use cloud-native policy enforcement tools: Leverage services like AWS Config, Azure Policy, or Google Cloud Security Command Center.
- Establish baseline configurations based on CIS Benchmarks: These benchmarks offer industry-standard secure configuration guidelines.
- Implement automated remediation for critical misconfigurations: Prioritize high-impact vulnerabilities for automated fixing.
- Conduct regular compliance audits and gap assessments: Identify and address any compliance gaps proactively.
- Use resource tagging for security classification and ownership: This simplifies management and improves visibility.
Popularized By:
- AWS Config and AWS Control Tower
- Azure Policy and Azure Security Center
- Google Cloud Security Command Center
- Terraform with Sentinel
- CloudFormation Guard
- Wiz
- Lacework
When and Why to Use This Approach:
Cloud configuration and compliance management is essential for any organization using cloud services, particularly for startups and enterprises in the IN region facing increasing regulatory scrutiny. It’s especially beneficial for those handling sensitive data and needing to meet strict compliance requirements. Implementing these practices early in your cloud journey helps establish a strong security foundation and prevents costly security incidents down the line. This proactive approach saves time, resources, and protects your reputation in the long run.
7. Data Loss Prevention and Backup Strategies
Data loss can be devastating for any organization, especially in the cloud where data resides outside your direct physical control. Therefore, robust Data Loss Prevention (DLP) and backup strategies are fundamental cloud security best practices for businesses of all sizes, from startups to established enterprises. This dual approach ensures your data is protected from various threats, including accidental deletion, ransomware attacks, hardware failures, and natural disasters, while simultaneously maintaining business continuity and facilitating disaster recovery. This is why it’s a crucial element of any comprehensive cloud security posture.
DLP focuses on identifying, monitoring, and protecting sensitive data before it’s lost. This involves implementing technologies and processes that classify data based on sensitivity (e.g., personally identifiable information, financial data, intellectual property), define policies for data handling and movement, and enforce these policies through automated controls. For example, a DLP policy might prevent sensitive data from being emailed outside the organization or uploaded to an unsanctioned cloud storage service.
Complementing DLP, a solid backup strategy ensures that even if data is lost or compromised, it can be recovered quickly and efficiently. This involves creating multiple copies of your data, storing them on different media types (and ideally in different locations), and regularly testing the restoration process.
Features and Benefits of DLP and Backup:
- Content Inspection and Classification: DLP solutions automatically scan data, both at rest and in transit, to identify and classify sensitive information.
- Policy-Based Controls for Data Movement: Define granular policies that control how data can be accessed, used, and shared.
- Automated Data Discovery and Classification: Regularly scan cloud environments to automatically discover and classify sensitive data stores, even as your data landscape evolves.
- Immutable Backups: Create backups that cannot be modified or deleted, even by ransomware, providing an uncompromised recovery point.
- Cross-Region Replication: Replicate data across multiple geographic regions to protect against regional outages and ensure data availability.
- Point-in-Time Recovery: Restore data to a specific point in time, allowing you to revert to a state before a data corruption or ransomware event.
- Backup Validation and Testing: Regularly validate and test your backup and recovery procedures to ensure they function as expected when needed.
Pros:
- Prevents unauthorized data exfiltration: DLP controls prevent sensitive data from leaving the organization without proper authorization.
- Protects against ransomware and accidental deletion: Immutable backups and robust recovery processes provide a safety net against data loss.
- Ensures business continuity and disaster recovery: Fast and reliable recovery minimizes downtime and ensures business operations can continue in the event of a disaster.
- Helps maintain regulatory compliance: DLP and backup solutions help organizations meet data protection and privacy regulations.
Cons:
- Can impact performance if overly restrictive: Overly aggressive DLP policies can sometimes hinder legitimate data access and workflows.
- Storage costs for comprehensive backup strategies: Maintaining multiple copies of data, particularly in different regions, can increase storage costs.
- Complexity in managing data across multiple environments: Managing data backups across multiple cloud environments and on-premises systems can be complex.
- Potential false positives in DLP controls: DLP systems can sometimes flag legitimate data transfers as suspicious, leading to false positives.
Examples of Successful Implementation:
- Netflix relies on automated multi-region backups to ensure service availability and protect its vast content library.
- Salesforce employs robust DLP controls to safeguard customer data and maintain its reputation for security and trust.
- Financial institutions increasingly implement immutable backups to protect against the growing threat of ransomware attacks.
Actionable Tips:
- Implement the 3-2-1 backup strategy: Maintain 3 copies of your data on 2 different media types, with 1 copy stored offsite.
- Use automated data discovery to identify sensitive data stores: Continuously scan your cloud environments to identify and classify sensitive data.
- Implement immutable backups that cannot be altered or deleted: This crucial step safeguards your backups from ransomware and malicious actors.
- Regularly test backup restoration processes: Ensure you can recover your data quickly and effectively when needed.
- Configure point-in-time recovery for critical databases: This allows you to revert to a specific point in time before a data corruption incident.
- Encrypt backups and manage keys securely: Protect your backups with strong encryption and ensure your encryption keys are properly managed.
Popularized By:
Solutions like AWS Backup and Macie, Azure Information Protection and Backup, Google Cloud Data Loss Prevention, along with third-party vendors like Veeam, Cohesity, and Rubrik, provide the tools and capabilities needed to implement robust DLP and backup strategies.
By implementing comprehensive data loss prevention and backup strategies, organizations in the IN region can effectively mitigate the risks of data loss, protect their valuable information assets, and ensure business continuity. These practices are essential components of any cloud security best practices framework and are vital for organizations of all sizes and across all industries.
8. Security Incident Response and Disaster Recovery
Security incidents and disasters are an unfortunate reality in today’s interconnected world. For businesses operating in the cloud, a robust Security Incident Response and Disaster Recovery (SIRP/DR) plan is not just a best practice—it’s essential for survival. This critical aspect of cloud security best practices helps organizations prepare for, respond to, and recover from security breaches, service disruptions, and other unforeseen events, minimizing downtime and mitigating potential damage. This is crucial for maintaining business continuity, preserving customer trust, and protecting your reputation.
What is it and how does it work?
SIRP/DR in a cloud environment involves a structured approach encompassing six key phases:
- Preparation: Establishing proactive measures like security audits, vulnerability assessments, and establishing a well-defined incident response plan.
- Detection: Implementing monitoring and alerting systems to identify suspicious activities and potential security breaches quickly.
- Containment: Isolating affected systems and limiting the spread of the incident to prevent further damage.
- Eradication: Removing the root cause of the security incident or disaster, such as malware or a misconfiguration.
- Recovery: Restoring affected systems and data to their pre-incident state.
- Post-Incident Analysis: Reviewing the incident to identify lessons learned and improve future response efforts.
Features of an effective SIRP/DR plan:
- Incident Response Automation: Automating tasks like isolating affected systems, blocking malicious traffic, and initiating backups speeds up response time and reduces the burden on security teams.
- Playbooks for Common Security Scenarios: Pre-defined procedures for handling specific types of incidents (e.g., DDoS attacks, ransomware) ensure a consistent and effective response.
- Cross-Functional Response Teams: Establishing teams with representatives from different departments (IT, security, legal, PR) facilitates coordinated and efficient incident management.
- Disaster Recovery as a Service (DRaaS): Leveraging cloud-based DRaaS solutions for rapid failover and recovery of critical systems and data.
- Table-top Exercises and Simulations: Regularly testing the SIRP/DR plan through simulated scenarios helps identify weaknesses and improve preparedness.
- Post-Incident Analysis and Improvement: Learning from past incidents is crucial for refining processes and strengthening security posture.
Examples of Successful Implementation:
- Capital One’s 2019 data breach, while highlighting the importance of security, also demonstrated the importance of having a response plan in place. While the breach was significant, their response and subsequent analysis helped them strengthen their security posture.
- Zoom’s rapid security response during the COVID-19 usage surge showed how a proactive approach to incident response and scaling infrastructure can help maintain service availability during unexpected events.
- Azure’s regional outage recovery procedures highlight the robustness of cloud providers’ own DR plans, offering a model for businesses to follow.
Actionable Tips for Implementation:
- Develop cloud-specific incident response playbooks: Consider the unique characteristics of your cloud environment.
- Implement automation for common response actions: This will save valuable time during a crisis.
- Conduct regular tabletop exercises and simulations: Practice makes perfect, even in incident response.
- Establish clear roles and responsibilities across teams: Ensure everyone knows their role in a crisis.
- Implement forensic readiness with appropriate logging: Detailed logs are critical for investigating incidents.
- Test disaster recovery procedures at least quarterly: Regular testing ensures your DR plan remains effective.
- Define recovery time objectives (RTO) and recovery point objectives (RPO): These metrics define your acceptable downtime and data loss thresholds.
Pros and Cons:
Pros:
- Reduces impact and cost of security incidents
- Minimizes downtime during disasters
- Builds organizational resilience
- Provides assurance to customers and stakeholders
Cons:
- Requires ongoing investment in preparation and testing
- Cloud-specific response challenges differ from on-premises
- Coordination complexity in multi-cloud environments
- Potential skills gaps for cloud-specific incidents
Why this deserves a place in the list:
In the IN region, where the digital economy is rapidly expanding and reliance on cloud services is increasing, having a strong SIRP/DR plan is non-negotiable. It’s a foundational element of cloud security best practices because it addresses the inevitable: incidents will happen. By being prepared, you can minimize the damage, recover quickly, and maintain the trust of your customers and stakeholders. This practice ensures that organizations can respond effectively to a wide range of events, protecting their operations and reputation in the face of adversity. Investing in SIRP/DR is investing in the long-term health and success of your business in the cloud.
Top 8 Cloud Security Best Practices Comparison
| Best Practice | Implementation Complexity | Resource Requirements | Expected Outcomes | Ideal Use Case | Key Advantages |
|---|---|---|---|---|---|
| Identity and Access Management (IAM) | Medium – requires policy design and ongoing maintenance | Moderate – skilled admin and audit resources | Strong access control and compliance audit trails | Enterprise-wide access control and privilege management | Reduces unauthorized access; fine-grained permissions |
| Data Encryption | Medium – involves integration with key management | Moderate to high – key management and cryptography expertise | Protects data integrity and confidentiality | Protecting sensitive data at rest, in transit, and in use | Protects data even if other controls fail; compliance aid |
| Network Security and Segmentation | High – complex network and policy design | High – network architecture and security specialists | Limits breach impact; granular traffic control | Workload isolation, hybrid cloud, regulatory segmentation | Limits blast radius; defense-in-depth |
| Continuous Security Monitoring and Threat Detection | High – requires tool integration and skilled analysts | High – log storage, processing power, and staff | Rapid incident detection and response | Real-time threat detection in complex cloud environments | Improves visibility; detects sophisticated threats |
| Automated Security Testing and Vulnerability Management | Medium to high – integration into CI/CD pipelines | Moderate – automation tools and developer buy-in | Early vulnerability identification and remediation | DevSecOps environments; CI/CD security gates | Reduces remediation cost; consistent security standards |
| Cloud Configuration and Compliance Management | Medium – policy development and enforcement | Moderate – automation tools and compliance expertise | Continuous compliance and configuration assurance | Prevention of misconfiguration and compliance drift | Prevents misconfigurations; automates compliance |
| Data Loss Prevention and Backup Strategies | Medium – setup and regular testing required | Moderate to high – storage, backup systems, classification | Data protection and disaster recovery readiness | Sensitive data protection and ransomware defense | Ensures business continuity; protects data integrity |
| Security Incident Response and Disaster Recovery | High – planning, automation, and team coordination | High – response teams, toolsets, and training | Minimized downtime and damage from incidents | Incident handling and disaster recovery in cloud environments | Reduces impact and cost of incidents; builds resilience |
Staying Ahead of the Curve
Mastering cloud security best practices is no longer a luxury, but a necessity for organizations of all sizes. From startups to enterprises, robust cloud security is paramount for protecting sensitive data, maintaining business continuity, and fostering trust with customers. This article has covered key aspects of building a secure cloud environment, including Identity and Access Management (IAM), data encryption, network security and segmentation, continuous security monitoring, automated security testing, cloud configuration and compliance management, data loss prevention and backup strategies, and incident response planning. These practices, when implemented effectively, form the bedrock of a comprehensive cloud security posture.
Implementing strong cloud security best practices is crucial for protecting your valuable data. For a deeper dive into website security specifically, check out this helpful resource: 10 best practices for website security. Focusing on these core areas and consistently evaluating your security measures will ensure you’re well-equipped to handle evolving threats. Furthermore, prioritizing cloud security best practices contributes to regulatory compliance, which is especially critical in today’s increasingly regulated digital landscape.
The value of these practices extends beyond mere protection; they empower your business to innovate and grow with confidence. By proactively addressing security risks and vulnerabilities, you can free up resources to focus on core business objectives and drive digital transformation. The dynamic nature of the cloud requires a vigilant and adaptive approach. By embracing cloud security best practices, you’re not just protecting your data today—you’re building a foundation for sustainable success in the cloud-powered future.
Ready to fortify your cloud security and navigate the complexities of the cloud landscape? Signiance Technologies provides comprehensive cloud security solutions tailored to your specific needs, helping you implement and manage these best practices effectively. Visit Signiance Technologies today to learn more about how we can empower your cloud security journey.
