Understanding India's Cloud Security Compliance Reality
Cloud security compliance is no longer a mere checkbox for Indian businesses. It's a crucial part of doing business in our interconnected world, especially with India's evolving regulatory landscape. Discussions with compliance officers and security leaders reveal a common theme: organizations face significant challenges in navigating this complex environment.
Traditional Security Falls Short
Traditional security measures, originally designed for on-premises infrastructure, often struggle to keep up with the dynamic nature of the cloud. Cloud environments introduce new complexities like shared responsibility models and constantly evolving services. For example, misconfigured access controls, a common vulnerability in cloud deployments, can expose sensitive data if left unaddressed. Organizations must adapt their security strategies to effectively protect data and maintain compliance.
The Evolving Indian Landscape
The Indian cloud security landscape presents unique challenges and opportunities. The Indian Computer Emergency Response Team (CERT-In) guidelines, along with sector-specific requirements, demand close attention. The increasing use of cloud technologies across different industries adds another layer of complexity. Businesses need to stay up-to-date on the latest regulations and implement appropriate security measures. The landscape is a mix of challenges and opportunities. While overall cybersecurity incidents might have decreased, new threats like AI-driven attacks pose significant risks. The healthcare sector, for example, is a prime target, experiencing 21.8% of all attacks. In 2023, India ranked fifth globally in breached accounts, with 5.3 million accounts compromised. India is actively collaborating internationally, with memoranda of understanding with countries like Singapore and Japan, to bolster its cybersecurity defenses. For more in-depth statistics, see: Chambers.com
Global Standards Meet Local Requirements
Global standards like ISO 27001 and SOC 2 provide a valuable framework. However, they need to be adapted to comply with India-specific regulations, including requirements from the Personal Data Protection Bill, 2022. Successfully integrating these standards means understanding both global best practices and local regulatory expectations to achieve a comprehensive and compliant security posture. Further reading: How to master cloud security standards
Building a Compliance Strategy That Works
Organizations succeeding in this complex environment are building practical, not just theoretical, compliance strategies. This means moving beyond simple checklists and generic policies. They're creating frameworks that work in real-world situations. Key elements include:
-
Robust Governance Structures: Clearly defining roles and responsibilities for cloud security.
-
Effective Risk Assessment: Identifying and prioritizing actual threats to data and systems.
-
Comprehensive Documentation: Maintaining auditable records of security controls and processes.
By focusing on these core components, businesses can build a strong foundation for long-term cloud security compliance success.
Why Nearly Half Of Indian Companies Fail Cloud Audits
Cloud audit failures are a growing concern for Indian businesses. They pose a significant threat to an organization's reputation, operational continuity, and bottom line, not to mention regulatory headaches. This begs the question: why are so many Indian companies falling short?
The High Cost of Non-Compliance
Failing a cloud security audit is about more than just regulatory fines. The true costs extend much further, impacting a business in many ways. Customer trust can erode quickly following a data breach, leading to lost revenue and damage to brand image. Operational disruptions caused by security incidents can halt productivity and impact service delivery. Compliance failures can also create a competitive disadvantage, making it difficult to attract investors and partners.
Common Pitfalls in Cloud Audits
Several factors contribute to cloud audit failures. Misconfigured access controls are a key vulnerability. This means employees may have access to sensitive data they shouldn't, creating exploitable weaknesses. Inadequate documentation is another common problem. Without clear documentation of security processes and controls, demonstrating compliance to auditors becomes a challenge. A lack of continuous monitoring can also lead to undetected security gaps and slow incident response.
In India, the importance of cloud security compliance is underscored by the high rate of audit failures. A concerning 49% of Indian respondents in a 2022 Asia Pacific survey reported failing a cloud security audit. This highlights the critical need for stricter compliance measures and more robust security practices to prevent misconfigurations and data breaches. For further insights into these statistics, visit Get Astra.
Turning Failures into Learning Opportunities
While audit failures are setbacks, they also present valuable learning opportunities. Organizations that embrace this perspective can analyze the root causes of their failures and implement corrective actions. This could involve strengthening access controls, improving documentation practices, or investing in automated security tools.
Building an Audit-Ready Culture
Leading organizations are moving beyond reactive compliance and building proactive, audit-ready cultures. They view compliance as a competitive advantage, not a burden. This cultural shift includes:
- Integrating security into every stage of the cloud lifecycle.
- Providing regular security awareness training to employees.
- Fostering a culture of continuous improvement and adaptation.
Proactive Compliance: A Strategic Advantage
By embedding cloud security compliance into their core operations, Indian companies can not only avoid costly audit failures but also enhance their overall security posture. This proactive approach builds resilience, strengthens customer trust, and positions the organization for sustainable growth in the cloud. It means moving beyond simple checklists and embracing cloud security compliance as a continuous journey of improvement and adaptation. Through proactive measures and a commitment to strong security practices, businesses can transform cloud compliance from a burden into a strategic advantage, strengthening their operations, building customer trust, and achieving long-term success. Understanding the common pitfalls and taking proactive steps to address them is vital for establishing a robust cloud security posture and attaining lasting compliance success.
Building Your Bulletproof Compliance Framework
Building a robust cloud security compliance framework goes beyond simple checklists and generic policies. This is particularly true in India, where dynamic cloud environments are increasingly common. This section explores the key components that separate truly effective compliance programs from those that only look good on paper.
Establishing Governance Structures
First, establish clear governance structures that can scale with your business growth. This means defining roles, responsibilities, and reporting procedures for cloud security. For example, assign specific individuals accountability for data security, access control, and ongoing compliance monitoring. This clarity ensures everyone understands their contributions to maintaining a secure cloud environment. For further insights, check out our Cloud Security Assessment Checklist.
Implementing Risk Assessment
Next, implement risk assessment methodologies that pinpoint actual threats. Go beyond hypothetical scenarios and focus on risks specific to your industry and cloud deployments. Factors to consider include data sensitivity, access vulnerabilities, and potential attack vectors. This focused approach allows for the effective prioritization of security efforts.
Creating Effective Documentation
Thorough documentation is also essential. This isn't simply for satisfying auditors; it's a valuable resource for your operational teams. Document security policies, procedures, and controls in a clear, accessible format. This documentation should fulfill audit requirements while serving as a practical guide for your team.
Adapting to Changing Regulations
The regulatory landscape is constantly evolving, especially in India with regulations like those from CERT-In. Design flexible frameworks that can adapt without requiring complete overhauls. Modular frameworks allow you to integrate new regulations and security best practices incrementally. This agility is critical for maintaining compliance in a dynamic regulatory environment.
Managing Multi-Cloud Environments
Many organizations in India operate in hybrid and multi-cloud environments, adding another layer of complexity to compliance management. Implement strategies that ensure consistent security and compliance across all platforms. This might involve using centralized management tools and implementing platform-agnostic security policies.
The following infographic highlights key vulnerabilities in cloud security:
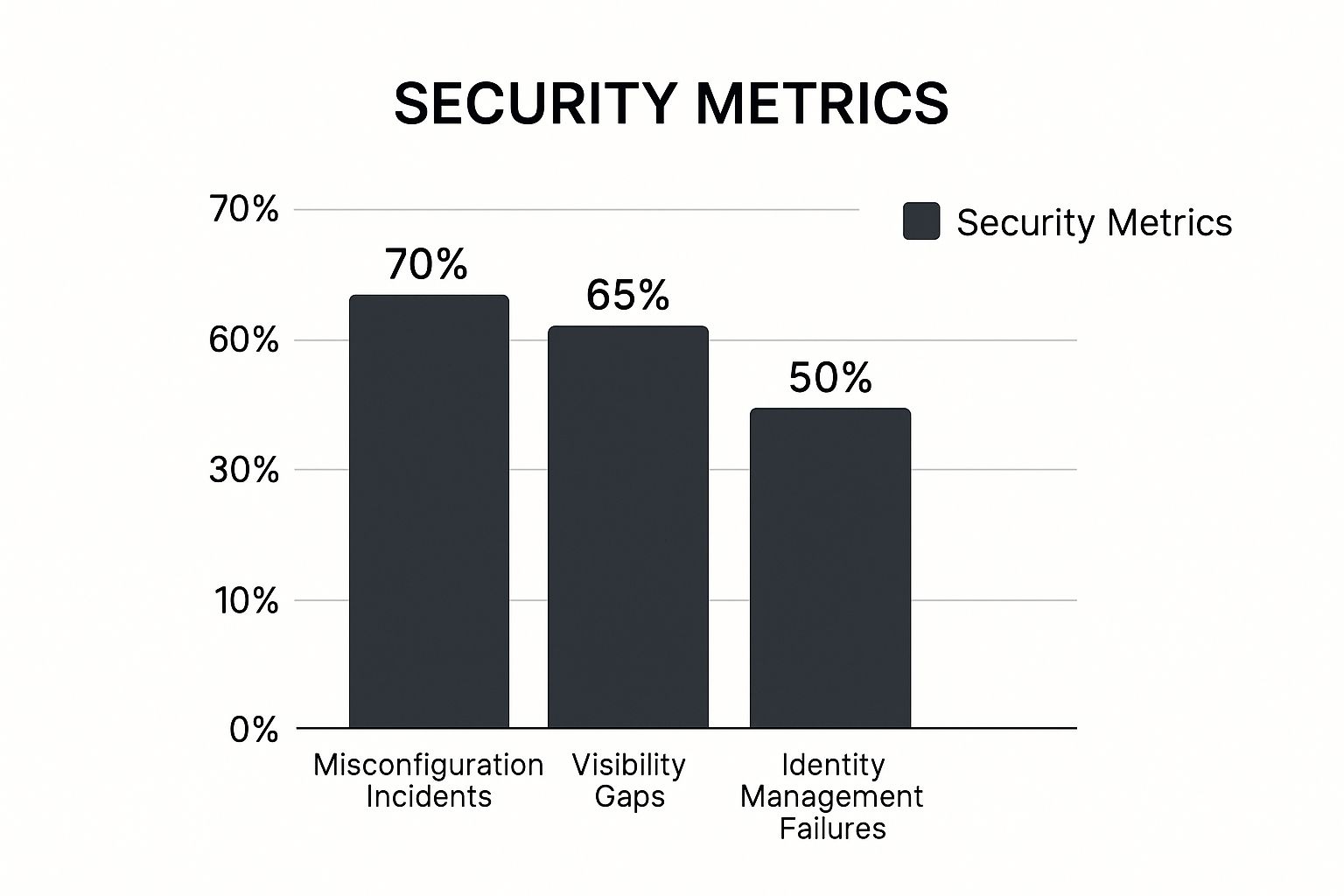
As the infographic shows, misconfiguration incidents represent 70% of vulnerabilities, followed by visibility gaps at 65% and identity management failures at 50%. This underscores the importance of strong security configurations, comprehensive monitoring tools, and robust identity management practices. Addressing these key vulnerabilities significantly strengthens an organization's cloud security posture and enhances overall compliance.
To help organizations navigate these complexities, let's examine some essential compliance frameworks:
Understanding the nuances of these frameworks is crucial for achieving and maintaining compliance in the Indian market. This table provides a starting point for Indian organizations to evaluate which frameworks best align with their specific needs and industry requirements.
| Framework | Key Requirements | Industry Focus | Implementation Timeline |
|---|---|---|---|
| ISO 27001 | Information security management system (ISMS), risk assessments, security controls | General, applicable to all sectors | Ongoing, requires regular audits and reviews |
| SOC 2 | Security, availability, processing integrity, confidentiality, privacy | Technology and cloud service providers | Varies based on scope, typically 6-12 months |
| PCI DSS | Data security standards for protecting cardholder data | Organizations handling payment card information | Ongoing, requires annual assessments |
| HIPAA | Protecting sensitive patient health information | Healthcare sector | Ongoing, requires continuous compliance efforts |
By understanding these frameworks and tailoring their implementation to their specific circumstances, businesses can build a more robust security posture and ensure ongoing compliance. A comprehensive approach to cloud security compliance, incorporating these elements, is essential for protecting your data, maintaining customer trust, and achieving lasting success in India’s digital ecosystem.
Navigating India's Complex Regulatory Maze

Building a robust cloud security compliance strategy in India requires a deep understanding of the country's regulatory landscape. It’s not simply a matter of checking off boxes; businesses need a proactive approach that addresses the specific requirements of Indian regulations. This means moving beyond generic policies and crafting strategies based on what truly matters for compliance in India.
Understanding CERT-In Guidelines
The Indian Computer Emergency Response Team (CERT-In) plays a vital role in establishing cybersecurity standards and guidelines. Understanding these guidelines is essential for any organization operating in the cloud within India. CERT-In directives cover various aspects of cloud security, including incident reporting, vulnerability management, and data retention.
Staying informed about the latest CERT-In updates is crucial for maintaining compliance. This requires diligent monitoring of official announcements and a commitment to adapting security practices accordingly.
Sector-Specific Requirements
India's regulatory environment also includes sector-specific requirements. For example, the financial services sector faces stringent regulations related to data privacy and security. The healthcare sector must also comply with regulations akin to HIPAA for protecting sensitive patient information.
Understanding these industry-specific regulations is critical for tailoring your cloud security compliance framework effectively. A one-size-fits-all approach simply won't work in India's diverse regulatory landscape.
Data Protection Legislation in India
The evolving data protection legislation in India, including updates related to the Personal Data Protection Bill, adds another layer of complexity to cloud security compliance. These regulations dictate how organizations collect, store, and process personal data of Indian residents.
Businesses must implement appropriate security measures to protect this data and comply with the evolving legal framework. This includes robust access controls, encryption, and data loss prevention strategies.
Economic Impact of Non-Compliance
The economic impact of overlooking cloud security compliance is significant. Gartner predicts that by 2025, end-user spending on information security in India will reach $3.3 billion, a 16.4% year-over-year increase. This rise is driven by persistent security challenges, data breaches, and the evolving regulatory landscape. For more detailed statistics, see this Gartner report.
Practical Implications for Cloud Deployments
Interpreting regulatory guidance in the context of specific cloud deployments is essential. This means understanding how regulations apply to your chosen cloud provider, your data storage practices, and your access control mechanisms.
For instance, if you store sensitive customer data in a cloud hosted outside of India, you must ensure your practices align with data localization requirements. Careful consideration of these factors is crucial for achieving and maintaining compliance.
Building Relationships With Regulators
Successful organizations in India often prioritize building relationships with regulatory bodies. This proactive approach fosters open communication and ensures a clear understanding of regulatory expectations. By engaging with regulators, businesses can stay ahead of changes and adapt their compliance strategies as needed.
This can involve participating in industry consultations and seeking expert advice from legal and compliance professionals specializing in Indian regulations. This forward-thinking approach helps businesses avoid costly violations and build sustainable, long-term compliance programs. These relationships can be invaluable in navigating the intricacies of India’s regulatory environment and ensuring long-term compliance success.
Making The Business Case For Security Investment

Justifying security investments requires a compelling business case. This means speaking the language of executives: focusing on the bottom line. This section explores the economic factors driving India's increasing security spending and how to build a business case that clearly demonstrates return on investment (ROI). You might be interested in: How to master security compliance.
Calculating the True Cost of Security Incidents
The first step is quantifying the potential financial impact of security incidents. This goes beyond the immediate costs like regulatory fines and data recovery. It's essential to consider the long-term damage to brand reputation, the loss of customer trust, and potential legal liabilities.
A data breach, for instance, can lead to significant customer churn and make attracting new business more difficult. Additionally, consider the operational disruptions caused by security incidents, including downtime, lost productivity, and the costs associated with incident response. Quantifying these costs provides a solid foundation for demonstrating the value of proactive security measures.
Demonstrating the ROI of Prevention
Once you’ve calculated the potential cost of incidents, you can effectively demonstrate the ROI of security investments. Compare the cost of preventive measures with the potential cost of a breach. Investing in robust cloud security compliance tools, for example, might seem expensive initially.
However, it is significantly less than the cost of a major data breach. This comparison reframes security as a strategic investment, protecting the organization’s financial well-being, rather than a cost center. This shift in perspective is essential for gaining executive buy-in.
Exploring Innovative Funding Models
Funding comprehensive security programs can be a challenge, particularly for organizations with limited budgets. Explore innovative funding models that enhance accessibility. A phased approach, for example, allows for prioritizing essential security measures initially and gradually expanding the program.
Another strategy is integrating security costs into project budgets, rather than treating them as a separate expense. This approach ensures that security is viewed as an integral part of every project from the start.
Cost-Optimization Strategies
Implementing cost-optimization strategies maximizes the impact of security investments. This can involve leveraging cloud-native security tools and services, often more cost-effective than traditional on-premises infrastructure. Negotiating favorable contracts with security vendors can also help reduce costs.
Further, consolidating security tools can streamline operations and minimize licensing fees.
Communicating Security Value to Stakeholders
Communicating the value of security to stakeholders requires focusing on business outcomes, not technical jargon. Instead of discussing intrusion detection rates, for example, emphasize how security investments reduce the risk of financial loss and safeguard brand reputation.
The economic impact of neglecting cloud security compliance is substantial. Gartner forecasts that end-user spending on information security in India will reach $3.3 billion in 2025, a 16.4% increase from the previous year. This growth reflects the increasing awareness of the financial consequences of security breaches and the evolving regulatory environment. Find more detailed statistics here.
By quantifying the value of security and presenting it in business terms, you effectively demonstrate its importance to decision-makers and secure necessary resources for a robust cloud security compliance program. This positions security as a business enabler, aligning security goals with overall business objectives. Through this comprehensive approach, security becomes a key component of a successful business strategy.
Continuous Monitoring That Actually Works
Forget set-and-forget security tools that generate more noise than value. True cloud security compliance in India demands continuous monitoring that provides actionable insights, not just alerts. This section reveals how to build a monitoring and incident response system that strengthens your security posture while meeting compliance requirements.
Balancing Automation and Human Analysis
Effective monitoring relies on the right balance of automated tools and human expertise. Automated systems can efficiently scan for misconfigurations and suspicious activity. However, human analysis is crucial for interpreting these findings and responding effectively. Think of it like a smoke detector: it alerts you to potential danger, but you still need to investigate the source and take appropriate action.
For example, an automated system might flag unusual login activity. A security analyst can then determine whether it’s a genuine threat or just an employee accessing their account from a new location. Finding this balance ensures that potential threats are identified and addressed accurately.
Establishing Effective Alerting
Bombarding your team with constant alerts leads to alert fatigue, where genuine threats can be missed. Instead, prioritize alerts based on severity and potential impact. This means configuring your monitoring tools to focus on critical events and filtering out less important notifications.
This targeted approach ensures your team can focus on addressing the most urgent security issues. By reducing noise and prioritizing critical alerts, you can improve response times and minimize the risk of overlooking real threats.
Building Incident Response Procedures
A well-defined incident response plan is essential for minimizing the impact of security events. This plan should outline clear steps for identifying, containing, and eradicating threats. It's crucial to establish clear communication channels and designate roles and responsibilities within the incident response team.
For example, the plan should specify who is responsible for communicating with stakeholders, who leads the technical investigation, and who manages the recovery process. Having a clear plan ensures a coordinated and efficient response to security incidents.
Maintaining Audit Trails for Compliance
Demonstrating compliance during regulatory reviews requires meticulous record-keeping. Your monitoring system should generate detailed audit trails that document security events, configuration changes, and incident response activities. This documentation provides evidence of your compliance efforts and helps auditors verify your adherence to regulatory requirements.
Think of it like a meticulously maintained logbook: it provides a comprehensive record of your security operations and demonstrates your commitment to cloud security compliance. Accurate and detailed audit trails are crucial for demonstrating compliance and passing regulatory audits.
Learning from Real-World Incidents
Every security incident is a learning opportunity. After an incident, conduct a thorough post-mortem analysis to identify the root cause and implement corrective actions. This continuous improvement process strengthens your security posture over time.
For example, if a misconfiguration led to a breach, implement automated checks to prevent similar misconfigurations in the future. By turning security events into learning opportunities, you build a more resilient and compliant cloud environment.
Tools and Capabilities
Choosing the right tools is crucial for effective cloud security monitoring. The following table, "Cloud Security Monitoring Tools and Capabilities Matrix", provides a comprehensive overview of common monitoring tools, their key features, the compliance standards they support, and their deployment complexity. This information will help you choose tools aligned with your organization's specific needs and compliance requirements.
| Tool Category | Key Features | Compliance Standards Supported | Deployment Complexity |
|---|---|---|---|
| Cloud Security Posture Management (CSPM) | Identifies misconfigurations and compliance violations | ISO 27001, SOC 2, PCI DSS | Varies depending on the tool and environment |
| Intrusion Detection/Prevention Systems (IDPS) | Detects and blocks malicious activity | ISO 27001, PCI DSS | Can be complex, requiring careful configuration and tuning |
| Security Information and Event Management (SIEM) | Collects and analyzes security logs from various sources | ISO 27001, SOC 2 | Can be complex, requiring integration with various systems |
| Vulnerability Scanners | Identifies security vulnerabilities in applications and systems | ISO 27001, PCI DSS | Relatively straightforward deployment |
As shown in the table, various tools are available, each with its own strengths. Selecting the appropriate combination of tools is key to building a robust security monitoring system. By selecting tools that align with your specific needs and compliance requirements, you can build a comprehensive and effective cloud security monitoring strategy. This proactive approach strengthens your security posture, reduces the risk of breaches, and demonstrates your commitment to cloud security compliance in the Indian regulatory environment. By continuously monitoring, responding effectively, and learning from incidents, Indian businesses can turn security events into opportunities for improving their overall cloud security compliance posture.
Key Takeaways
Your journey through cloud security compliance in India doesn't end here. This section distills the essential steps you can take now to build and maintain a robust security posture. These takeaways provide a practical roadmap for achieving cloud security compliance success.
Prioritizing A Proactive Approach
Don't wait for an audit failure or security incident to spur you into action. Proactive compliance builds resilience and strengthens your organization's security foundation. This means integrating security into every stage of the cloud lifecycle, from design and development to deployment and maintenance.
-
Regularly Assess Risks: Conduct thorough risk assessments to identify potential vulnerabilities specific to your cloud deployments in India. Consider data sensitivity, access controls, and potential attack vectors.
-
Embrace Continuous Monitoring: Implement real-time monitoring tools like those offered by Splunk or Datadog that provide actionable insights. This requires a balance between automated detection and human analysis to interpret findings and respond effectively.
-
Develop an Incident Response Plan: Establish clear procedures for handling security incidents, including communication channels and defined roles. A coordinated response minimizes business disruption and ensures data protection.
Navigating India's Regulatory Landscape
Understanding and adhering to India-specific regulations is crucial. Staying informed about updates from CERT-In and sector-specific requirements ensures your organization remains compliant.
-
Stay Updated on CERT-In Guidelines: Actively monitor CERT-In directives related to incident reporting, vulnerability management, and data retention to maintain alignment with national cybersecurity standards.
-
Address Sector-Specific Needs: Tailor your compliance framework to your industry's specific regulations. For example, financial services and healthcare sectors face stricter requirements due to the sensitivity of the data they handle.
-
Engage with Regulators: Proactively build relationships with regulatory bodies to ensure open communication and a clear understanding of expectations. This allows your organization to adapt to changes and avoid costly violations.
Building A Strong Business Case
Justifying security investments requires demonstrating a clear return on investment (ROI). By quantifying the potential costs of security incidents, you can effectively present the value of preventive measures to stakeholders.
-
Calculate the Cost of Incidents: Go beyond regulatory fines and factor in the long-term impact of security incidents, including damage to reputation, customer churn, and potential legal liabilities.
-
Focus on Business Outcomes: Communicate security value in terms of business benefits, like reduced financial risk and enhanced brand reputation. This approach resonates with decision-makers who prioritize business objectives.
Compliance As A Competitive Advantage
Don't view compliance as a burden, but as an opportunity to differentiate your organization. A robust security posture builds trust with customers, attracts investors, and strengthens your brand image.
-
Build an Audit-Ready Culture: Foster a culture of continuous improvement and adaptation to evolving regulations. Integrate security into every level of the organization, from development practices to employee training.
-
Promote Transparency: Be transparent with customers about your security practices. Demonstrating a commitment to data protection builds confidence and establishes your organization as a trustworthy partner.
Practical Implementation
Turning these takeaways into action requires a structured approach. Start with a clear understanding of your current security posture and define measurable goals for improvement.
-
Conduct a Security Assessment: Assess your current security infrastructure and identify gaps. This will help you prioritize investments and tailor your compliance framework to address your specific needs.
-
Develop a Compliance Roadmap: Create a clear roadmap for implementing security controls, policies, and procedures. Set realistic timelines and allocate resources effectively to achieve your compliance objectives.
To help you embark on this journey, consider Signiance Technologies. We offer comprehensive cloud security compliance solutions tailored to the Indian regulatory landscape. Our expert team can help you navigate the complexities of cloud security and build a robust, compliant infrastructure. Learn more about how Signiance Technologies can empower your cloud security compliance strategy.
