Picture this: your cloud environment is a bustling, ever-expanding city. It has countless buildings (your apps and services), roads (networks), and access points (APIs and credentials). Cloud Security Posture Management (CSPM) is like having a state-of-the-art surveillance and response system for this entire city. It operates 24/7, tirelessly checking every door, window, and security gate for anything left unlocked or out of place.
What Is Cloud Security Posture Management?
In simple terms, Cloud Security Posture Management (CSPM) is a family of security solutions built to automatically find and fix risks across all your cloud platforms. It constantly scans your infrastructure on AWS, Azure, and Google Cloud for configuration mistakes that could easily lead to data breaches, failed compliance audits, or costly downtime.
Think of it as your cloud’s dedicated safety inspector. Your DevOps and engineering teams are pushing out new features and updates at lightning speed. In that fast-paced environment, it’s incredibly easy for small, seemingly harmless errors to creep in. A public S3 bucket holding sensitive data, an IAM role with far too many permissions, or a database port accidentally left open to the internet any one of these can become a major security disaster.
Trying to catch these issues with manual checks or once-a-quarter audits just doesn’t work anymore. The sheer size and constant change in modern cloud environments make it impossible. This is where CSPM truly proves its worth.
A CSPM platform shifts your security approach from being reactive to proactive. Instead of just cleaning up after a breach, you start preventing them by fixing the root cause the misconfiguration long before an attacker can find it.
The Mission of a CSPM Solution
The core job of any CSPM tool is to give you total visibility and control over your cloud estate. Without it, you’re essentially flying blind. Most organisations now use a mix of different cloud providers, which makes tracking every single resource and its settings by hand an unwinnable battle. A CSPM brings everything together into one unified dashboard to help you:
- Discover all your cloud assets: It continuously finds every single virtual machine, storage account, database, and serverless function you have, no matter which cloud provider it lives on.
- Pinpoint security risks: It automatically checks your cloud configurations against proven security standards and compliance frameworks like CIS Benchmarks, NIST, and PCI DSS.
- Prioritise what matters most: Not all alerts are created equal. A smart CSPM helps you zero in on the most critical threats first, sorting them by their potential business impact.
- Automate the fix: The best CSPM tools can automatically correct misconfigurations or offer simple, guided steps to resolve them. This dramatically shrinks the time it takes to secure a vulnerability.
This cycle of continuous monitoring is vital. Before you even deploy a tool like this, getting a clear picture of your current state is a smart first step. A formal cloud security assessment can establish that crucial baseline and show you exactly where to focus your efforts for a stronger security posture.
The massive shift to the cloud has made these tools absolutely essential. Market trends tell the same story: the global CSPM market was valued at around USD 5.55 billion in 2025 and is expected to surge to USD 10.31 billion by 2029. This incredible growth shows just how fundamental CSPM has become to protecting modern business infrastructure. You can learn more about the market forces behind this growth from recent industry analysis.
What Can a Modern CSPM Tool Actually Do for You?

To really get what Cloud Security Posture Management is all about, you have to look past the marketing buzzwords. A modern CSPM platform isn’t just another scanner it’s an integrated system built to bring order to the chaos of the cloud. These tools have a set of core capabilities that work together, turning abstract security policies into real-world guardrails for your infrastructure.
Think of it this way: a good CSPM isn’t just a list of features to tick off. It’s a foundational platform for proactive security. It’s what gives your teams the confidence to build and deploy at speed without constantly worrying about opening up new security holes. It’s the safety net for fast-paced development.
Get a Bird’s-Eye View of Your Entire Cloud Estate
You can’t protect what you don’t know you have. It’s an old saying, but it’s never been more true than in the cloud. With assets spread across multiple providers like AWS, Azure, and GCP, and covering everything from IaaS to PaaS, things get complicated fast. Resources are spun up and torn down in minutes, making manual tracking completely futile.
This is the first problem a CSPM solves, acting as a single source of truth for your entire cloud footprint. By connecting directly to your cloud provider APIs, it gives you a constantly updated inventory.
- Complete Asset Inventory: It automatically discovers and catalogues every last virtual machine, storage bucket, database, serverless function, and network rule.
- Relationship Mapping: Crucially, it doesn’t just give you a list. It shows you how assets are connected to each other and to the internet, giving you the context needed to understand real-world risk.
- Unified Dashboard: All of this information is pulled into one searchable interface, so you can stop jumping between different provider consoles to piece the puzzle together.
This comprehensive visibility is the absolute bedrock of effective cloud security. Without it, you’re essentially flying blind, and any security measures you take are based on guesswork and incomplete data.
Catch Misconfigurations Before They Become Breaches
Once you can see everything, the next job is to spot the silent killers of cloud security: misconfigurations. It’s well-known that simple configuration mistakes are a primary cause of cloud data breaches. In fact, some reports show they were the initial attack vector in 30% of cloud attacks in early 2024. These aren’t fancy, sophisticated exploits; they’re preventable slip-ups.
This is where a CSPM becomes your tireless, automated security analyst. It constantly scans every asset it finds, checking them against a massive library of security rules and industry best practices.
Imagine a DevOps engineer rolls out new infrastructure with a script. A tiny error in that script leaves a storage bucket with staging data publicly readable. A CSPM tool would flag this deviation almost instantly long before a bad actor stumbles upon it.
This proactive detection engine is what lets your teams find and fix vulnerabilities before they escalate into full-blown incidents. It’s always on the lookout for common but critical issues like overly permissive IAM roles, unencrypted data stores, or network ports left exposed to the internet.
Take the Pain Out of Compliance Monitoring
Meeting compliance standards like ISO 27001, PCI DSS, or other industry regulations is a massive headache for any organisation. Traditional audits are manual, incredibly time-consuming, and only give you a snapshot of your compliance at a single point in time. In the cloud, where your environment changes by the minute, that snapshot is outdated almost as soon as it’s taken.
CSPM platforms automate this entire process. They ship with pre-built policy packs that map technical controls directly to the requirements of major compliance frameworks.
| Framework | How CSPM Helps Automate Compliance |
|---|---|
| PCI DSS | Continuously monitors for secure network configurations and ensures cardholder data environments are properly segmented and encrypted. |
| ISO 27001 | Enforces access control policies, tracks security configurations, and generates detailed reports to provide evidence for auditors. |
| NIST CSF | Helps implement the ‘Protect’ and ‘Detect’ functions by applying security controls and continuously monitoring for security events. |
This capability fundamentally changes compliance from a dreaded, periodic event into a continuous, automated process. Your security team gets a real-time dashboard view of your compliance status. If a resource ever drifts out of line, they get an immediate alert. This makes audit preparation dramatically easier and can save hundreds of team hours that were once spent on manual evidence gathering.
The Strategic Benefits of a CSPM Program
Implementing a Cloud Security Posture Management (CSPM) program is about more than just patching technical holes; it’s a strategic move that fundamentally improves how your organisation operates. When you look past the feature lists, the real win is how CSPM changes your team’s mindset around security, efficiency, and governance. It’s the difference between constantly fighting fires and proactively preventing them from starting in the first place.
These benefits don’t exist in a vacuum. Instead, they create a positive ripple effect, strengthening your security, operations, and compliance efforts all at once.
Harden Security Proactively
The most immediate and critical benefit of a CSPM is its power to stop security incidents before they ever happen. In a typical setup, security teams are often the last to know, discovering a misconfiguration only after a breach or during a frantic pre-audit check. This leaves them perpetually on the back foot.
A good CSPM solution completely flips this dynamic. By constantly scanning your cloud estate, it pinpoints potential weaknesses almost as soon as they appear.
- Drastically Reduces Mean Time to Remediate (MTTR): Forget taking days or weeks to find and fix a problem. With automated detection and clear remediation steps, you can shrink that time down to mere minutes or hours.
- Shrinks the Attack Surface: Every open port, every over-privileged user account, and every unencrypted data store is a potential entry point. CSPM helps you systematically find and close these gaps, making you a much harder target.
- Fosters a Security-First Culture: When your DevOps teams get instant, contextual feedback on the security impact of their code, they start building security into their workflow from the very beginning. It becomes second nature.
This proactive approach doesn’t just prevent data breaches. It builds a more resilient and fundamentally secure foundation for every single application you run in the cloud.
The image below paints a clear picture of just how different the outcomes are when you compare a manual security approach to an automated, CSPM-driven one.
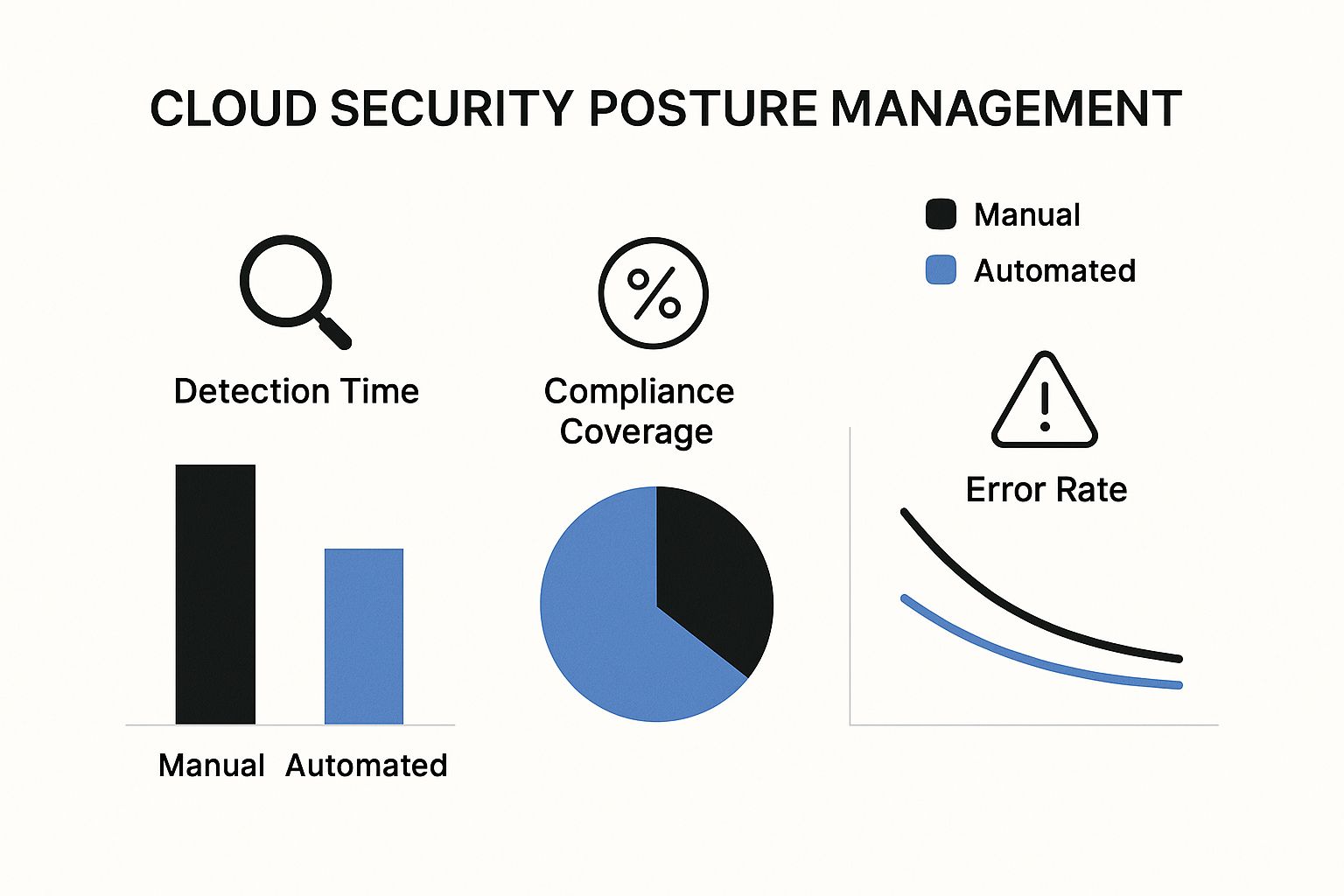
As the data shows, automation isn’t just a minor improvement it leads to a massive reduction in detection times and error rates while ensuring much broader compliance coverage.
Boost Operational Efficiency
Beyond the security wins, a CSPM programme brings huge operational efficiencies to the table. Manually checking configurations isn’t just slow; it’s a colossal waste of your most valuable asset: the time and talent of your cloud and security engineers.
By automating the repetitive, mind-numbing work of monitoring and assessment, CSPM frees up your experts. They can finally stop chasing down minor policy violations and start focusing on high-impact strategic work like threat hunting, architecting secure systems, and refining security processes.
This automation injects much-needed clarity and speed into workflows that used to get bogged down in cross-team friction. No more endless ticket back-and-forths between security and DevOps. Many issues can be fixed automatically or with guided, actionable steps, which naturally builds better collaboration.
Simplify and Automate Compliance
Let’s be honest: meeting compliance requirements is a necessary, but often painful, part of doing business. Proving you adhere to standards like PCI DSS, ISO 27001, or NIST can feel like a mad dash to gather evidence, consuming hundreds of hours.
A CSPM takes this periodic scramble and turns it into an automated, always-on process. These platforms are built with policy packs that map directly to the technical controls needed for major regulations. For a closer look at this, you can explore our detailed guide on cloud security standards and see how they work in practice.
The following table highlights the night-and-day difference between handling compliance manually versus with a CSPM.
Organizational Impact Before and After CSPM Implementation
| Area of Impact | State Before CSPM (Manual Approach) | State After CSPM (Automated Approach) |
|---|---|---|
| Security Risk | High. Relies on periodic, point-in-time checks, leaving long windows of exposure for misconfigurations. | Low. Continuous, real-time monitoring detects and flags risks within minutes, drastically reducing exposure time. |
| Operational Load | Heavy. Requires significant manual effort from security and DevOps teams to perform checks and gather evidence. | Light. Automation handles discovery, monitoring, and reporting, freeing up expert teams for strategic work. |
| Compliance Audits | Stressful and time-consuming. Involves a frantic, manual scramble to collect evidence, often revealing last-minute gaps. | Streamlined and audit-ready. Generates on-demand reports and provides a continuous view of compliance posture. |
Ultimately, bringing in a CSPM is an investment in stability, efficiency, and trust. It gives your teams the confidence they need to innovate quickly and securely in the cloud.
Overcoming Common CSPM Implementation Hurdles

Bringing a Cloud Security Posture Management (CSPM) solution into your organisation is a fantastic move for tightening up cloud security, but let’s be realistic it’s rarely a simple plug-and-play affair. Any time you introduce a significant new technology, you’re bound to hit a few bumps. The real trick is knowing what those bumps are ahead of time so you can navigate them smoothly.
The most common roadblocks aren’t just about technology; they’re about people and processes. You’re trying to weave a new tool into an already complex tech stack, handle a potential tidal wave of alerts, and get developers on board who might just see it as another roadblock. Thinking about these challenges from the start is the key to a rollout that helps your teams, rather than just adding to their workload.
Taming the Flood of Security Alerts
One of the first things you’ll likely experience after switching on a CSPM is what we call “alert fatigue.” The tool starts doing exactly what you bought it for finding every single misconfiguration, big and small. While that visibility is powerful, seeing hundreds or even thousands of issues can be completely paralysing. The danger here is that your teams become so swamped, they start ignoring everything, including the truly critical alerts.
You can’t boil the ocean. The secret is to prioritise intelligently. A good CSPM will help by giving you risk scores, but that’s only half the story. Your team’s own business context is the magic ingredient.
Think about it: a publicly exposed development server is a problem, but it’s nowhere near as urgent as a production database filled with customer data. Effective prioritisation means asking the right questions:
- What’s the real-world impact? Start with the vulnerabilities that could directly expose sensitive data or take down critical services.
- How easy is it to exploit? Focus on the low-hanging fruit for attackers the issues they can find and leverage with minimal effort.
- What’s the business context? Combine the tool’s technical risk score with your internal knowledge of what that asset actually does.
Filtering alerts through this lens turns a scary, overwhelming list into a focused, actionable plan. It ensures your engineers are always working on the fixes that matter most.
Integrating CSPM into Your Existing Workflow
A CSPM tool that lives on an island is a tool that will eventually be ignored. For it to be truly successful, it needs to fit snugly into the day-to-day work of your DevOps and security teams. If an engineer has to constantly switch context and log into yet another dashboard just to check for security issues, the tool becomes a chore, not a helper.
The goal is to bring the security findings to where your teams already are. This is the heart of the “shift-left” philosophy embedding security checks right into the development pipeline.
True integration means security becomes a natural part of building software, not a frustrating checkpoint at the very end. When a developer sees and fixes a security flaw directly in their CI/CD pipeline, you’ve won.
When choosing a CSPM, look for one with strong, out-of-the-box integrations for the tools you rely on:
- CI/CD Tools: Look for native support for tools like Jenkins or GitLab CI. This allows you to scan Infrastructure-as-Code (IaC) templates and catch problems before they ever get deployed.
- Ticketing Systems: Your CSPM should be able to automatically create tickets in platforms like Jira or ServiceNow, assigning them to the right team without any manual effort.
- Communication Platforms: Critical alerts should be piped directly into channels on Slack or Microsoft Teams for immediate visibility and response.
This deep integration breaks down the old silos between development and security, creating a culture where everyone owns a piece of the security puzzle.
Squeezing Every Drop of Value from Your CSPM Investment
So, you’ve got a Cloud Security Posture Management platform. That’s a great start. But just switching it on is like buying a high-performance sports car and only ever driving it to the local shops. To really get your money’s worth, you need to move beyond thinking of it as a simple monitoring tool. It needs to become the beating heart of your entire security programme.
Think of it this way: a basic setup is a smoke detector. A fully optimised CSPM is a comprehensive fire prevention and response system, complete with sprinklers, evacuation plans, and a direct line to the fire brigade. Its true power is unlocked when you ditch the default settings and start moulding it to the unique contours of your organisation’s environment. This means making it smarter, better connected, and woven into the fabric of your daily work.
Customise Policies to Fit Your Real-World Risks
Every business has a different appetite for risk. A sandbox for developers simply doesn’t carry the same weight as a production environment swimming with sensitive customer data. Relying on the generic, out-of-the-box policies that come with your CSPM is a decent first step, but it often leaves you with one of two problems: a flood of irrelevant alerts or gaping holes where you need the most scrutiny.
The key to unlocking real value is to customise your security policies. You need to build rules that genuinely reflect your business context and risk profile. For instance, while a standard policy might flag any open port, a custom rule can be far more intelligent. It could, for example, immediately classify an open SSH port on a production database server as a critical, hair-on-fire incident.
This targeted approach delivers huge benefits:
- Cuts through the noise: By zeroing in on what’s actually critical to your business, you stop your teams from drowning in a sea of low-impact findings.
- Sharpens your focus: Custom rules let you automatically crank up the severity for issues affecting your crown-jewel applications or data stores.
- Enforces your own standards: You can translate your company’s specific security gospel into code, ensuring it’s applied consistently across every cloud environment.
This level of customisation transforms your CSPM from a generic scanner into a savvy security guard that understands precisely what you need to protect most.
Plug Your CSPM into Your SIEM
Your CSPM is a goldmine of data about the health of your cloud infrastructure. But if that data sits all by itself in a silo, you’re missing the bigger picture. One of the most powerful moves you can make is to integrate your CSPM with your Security Information and Event Management (SIEM) system.
When you feed CSPM alerts into your SIEM, you create a single source of truth for your security operations. It pulls your posture data into the same view as other crucial signals, like network traffic and application logs, giving you a much richer context for spotting and investigating threats.
This integration is what allows your security team to connect the dots. They can correlate a cloud misconfiguration flagged by the CSPM with suspicious user activity logged by the SIEM to uncover sophisticated attacks that would otherwise fly completely under the radar. It turns isolated alerts into truly actionable intelligence.
Build Clear Workflows for Fixing Problems
Finding a security flaw is only half the job; actually fixing it is what really matters. A common reason CSPM initiatives fail to deliver is the lack of a clear, well-oiled process for remediation. When an alert goes off, who’s on the hook to fix it? How quickly does it need to be done? Without solid answers, critical alerts can get lost in a ticket queue for weeks, gathering digital dust.
To prevent this, you absolutely must establish documented remediation workflows. These aren’t just suggestions; they are the standard operating procedures that define:
- Ownership: Pinpoint the exact teams or individuals responsible for handling different types of alerts.
- Service Level Agreements (SLAs): Set concrete deadlines for acknowledging and resolving issues based on their severity.
- Escalation Paths: Clearly outline who gets the call if an issue isn’t fixed within its SLA.
A well-defined workflow creates accountability and injects a sense of urgency. When a critical issue pops up, everyone knows exactly what their role is, who they need to work with, and how fast they need to move. This operational discipline is the final piece of the puzzle that turns CSPM findings into a genuinely stronger, more resilient cloud security posture.
Understanding How CSPM Complements Other Security Tools

The cloud security world is a notorious alphabet soup, making it tough to figure out which tool does what. To really get a feel for what Cloud Security Posture Management brings to the table, it helps to see how it fits alongside the other tools in your security lineup. A CSPM isn’t a silver bullet that solves everything; think of it as a specialist that shines when it’s part of a well-coordinated team.
Let’s use an analogy. Imagine your cloud environment is a new building you’re constructing. Each security tool has a very specific job to do.
- CSPM (The Architectural Inspector): A CSPM is your building inspector. Its entire focus is on the blueprints and the core structure the cloud infrastructure itself. It’s looking for fundamental design flaws, like a fire escape that leads nowhere (a misconfigured network) or a main entrance with no lock (a publicly exposed storage bucket). It ensures the building is structurally sound before you even think about moving anything inside.
- CWPP (The Bodyguard): A Cloud Workload Protection Platform is the bodyguard hired to protect what’s inside the building. It isn’t concerned with the building’s architecture. Its job is to protect the valuable assets your applications, databases, and virtual machines from active threats while they are running.
- CASB (The Access Gatekeeper): A Cloud Access Security Broker is like the security guard at the front desk. It controls who comes in and out of specific rooms (your SaaS apps like Microsoft 365 or Salesforce) and what they’re allowed to do once they’re inside.
Together, these tools create a defence-in-depth strategy, covering everything from the foundational infrastructure to the applications running on top. You can dive deeper into these layered approaches in our guide to the top cloud security best practices to protect your data.
The Rise of Unified Platforms
Juggling all these separate tools can get complicated, which is why the industry is steadily moving toward unified platforms. You’ll hear them called Cloud-Native Application Protection Platforms (CNAPPs). At their core, a CNAPP bundles the capabilities of CSPM, CWPP, and other security tools into a single, cohesive solution.
A CNAPP’s main goal is to tear down the walls between different security functions. It offers a single pane of glass, connecting the dots between an infrastructure misconfiguration and an active threat on a workload, which gives your team far richer, more actionable intelligence.
This shift towards consolidation is particularly critical in fast-growing markets. In India, for example, the huge push for cloud adoption in sectors like banking, finance, and government has dialled up the need for watertight security. With complex hybrid and multi-cloud setups becoming the norm, automated posture management is no longer a nice-to-have it’s essential for meeting compliance mandates from bodies like CERT-In.
This is why the Indian Cloud Security Posture Management market is poised for significant growth, fuelled by nationwide digital initiatives that hinge on secure infrastructure. Understanding this trend towards unified platforms like CNAPP helps you build a security stack that’s ready for what’s next, not just what’s here today.
Frequently Asked Questions About CSPM
Even when the benefits of Cloud Security Posture Management are clear, teams often have practical questions when it’s time to actually pick and implement a solution. Let’s walk through some of the most common ones we hear from architects and DevOps teams who are new to CSPM.
Is CSPM Only for Large Enterprises?
Absolutely not. While it’s true that large organisations with vast multi-cloud estates get huge value from CSPM, smaller companies and startups can benefit just as much.
Think of it like this: building good security habits from day one is far easier than trying to fix years of accumulated “security debt” later on. A single, simple misconfiguration can be just as devastating for a small business as it is for a corporate giant, making a solid CSPM strategy a smart move for companies of any size.
How Is CSPM Different from a Vulnerability Scanner?
This is a great question, and it’s easy to see why people get them mixed up. Here’s a simple way to distinguish them:
- A vulnerability scanner is like a health inspector for your software. It looks inside your virtual machines and containers for known problems, such as an outdated library or an unpatched vulnerability (CVEs). Its job is to check the health of the workload itself.
- A CSPM tool acts more like a building inspector for the cloud infrastructure around your workload. It checks if the cloud service configurations things like firewall rules, identity and access management (IAM) permissions, and data encryption settings are set up securely.
Both are critical, but they focus on different layers of your security. A scanner answers, “Is the code running on this server safe?” A CSPM answers, “Is the cloud environment this server is running in configured correctly?”
CSPM is about securing the cloud infrastructure, while vulnerability scanning is about securing what you run in the cloud. You really need both for a proper defence-in-depth strategy.
Can We Just Use the Native Tools from AWS, Azure, or GCP?
The native tools offered by cloud providers, like AWS Security Hub or Microsoft Defender for Cloud (formerly Azure Security Center), are excellent starting points. They give you solid visibility within their own ecosystem. The problem arises when your operations span more than one cloud.
If your organisation uses a mix of AWS, Azure, and GCP, a dedicated, third-party CSPM becomes essential. It pulls all your security findings into one central dashboard. This gives you a single source of truth and a consistent set of rules for your entire cloud footprint, saving your team from the nightmare of juggling multiple consoles and trying to correlate data manually.
Ready to build a secure, resilient, and high-performing cloud foundation? The experts at Signiance Technologies can help. We specialise in designing and managing secure cloud architectures that let you innovate with confidence. Learn how we can strengthen your security posture by visiting us at signiance.com.
